A large-scale ad fraud operation called ‘Scallywag’ is monetizing pirating and URL shortening sites through specially crafted WordPress plugins that generate billions of daily fraudulent requests.
Scallywag was uncovered by bot and fraud detection firm HUMAN, which mapped a network of 407 domains supporting the operation that peaked at 1.4 billion fraudulent ad requests per day.
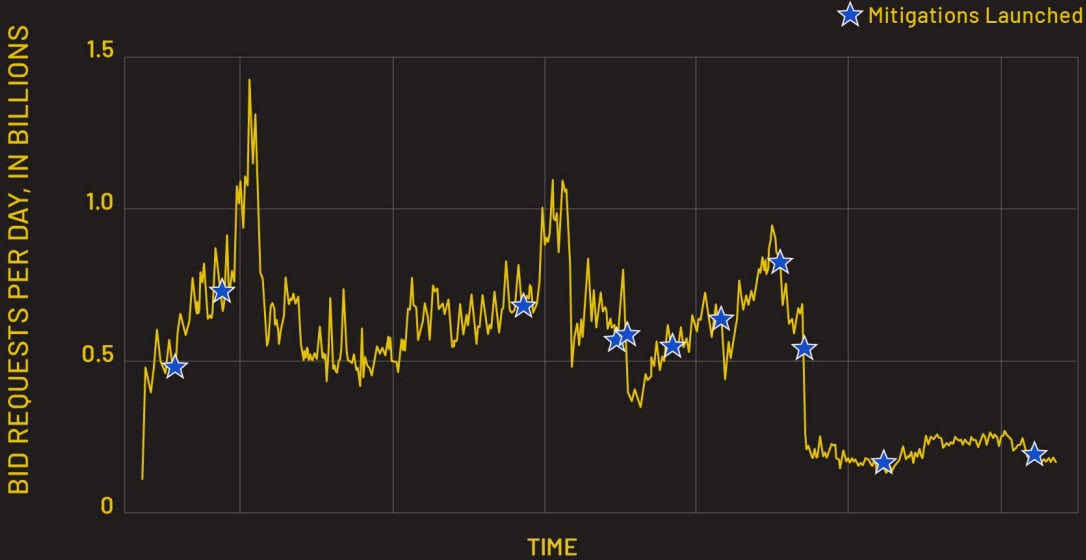
HUMAN’s efforts to block and report Scallywag traffic have resulted in its shrinking by 95%, although the threat actors have shown resilience by rotating domains and moving to other monetization models.
Built around WordPress ad fraud plugins
Legitimate ad providers avoid pirating and URL shortening sites due to legal risks, brand safety concerns, ad fraud, and lack of quality content.
Scallywag is a fraud-as-a-service operation built around four WordPress plugins that help cybercriminals generate money from risky and low-quality sites.
The WordPress plugins created by the operation are Soralink (released in 2016), Yu Idea (2017), WPSafeLink (2020), and Droplink (2022).
Human says multiple independent threat actors buy and use these WordPress plugins to set up their own ad fraud schemes, with some even posting tutorials on YouTube on how exactly to do it.
“These extensions lower the barrier to entry for a would-be threat actor who wants to monetize content that wouldn’t generally be monetizable with advertising; indeed, several threat actors have published videos to coach others on setting up their own schemes,” explains HUMAN.
Droplink is the only exception to the sales model, as it’s available for free by performing various money-making steps for the sellers.
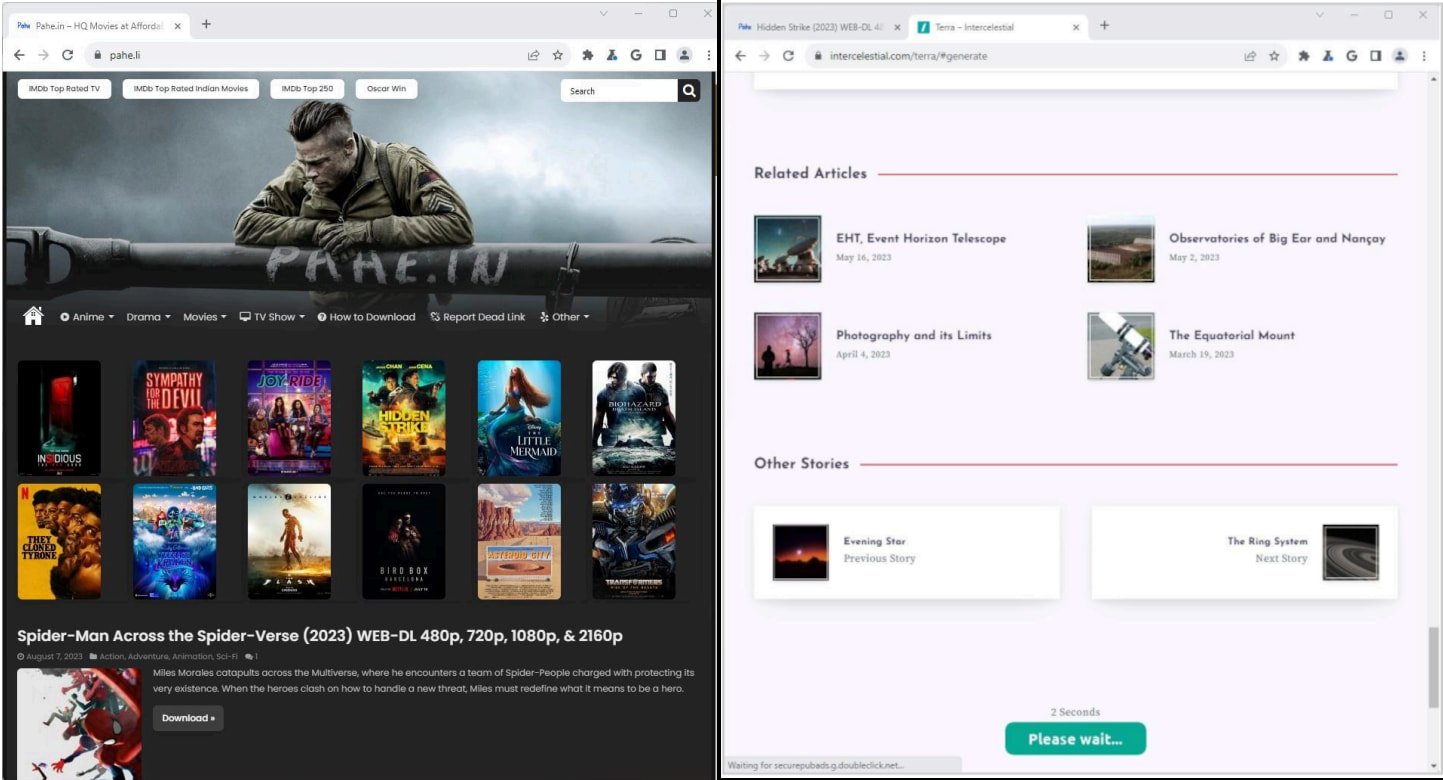
Users visiting piracy catalog sites to find movies or premium software click on embedded URL-shortened links and are redirected through the operation’s cashout infrastructure.
Piracy catalog sites that can’t directly host ads aren’t necessarily run by Scallywag actors. Instead, their operators form a ‘gray partnership’ with ad fraudsters to outsource monetization.
Source: HUMAN
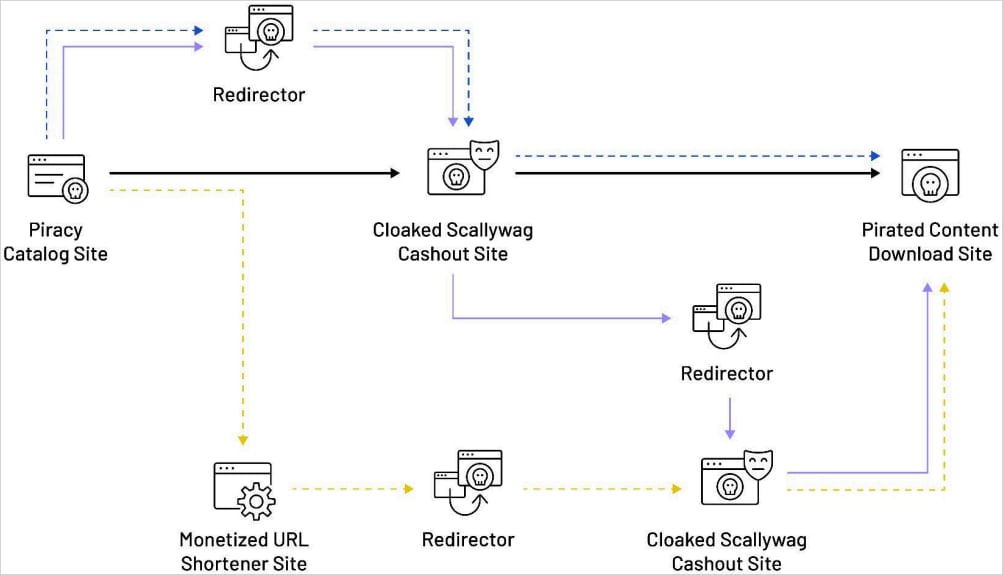
The redirection process takes the visitor through intermediary, ad-heavy pages that generate fraudulent impressions for the Scallywag operators, and end up on a page hosting the promised content (software or movie).
The intermediary sites are WordPress sites running the Scallywag add-ons. Those handle the redirect logic, loading of ads, CAPTCHA, timer, and the cloaking mechanism, which shows a clean blog on ad platform checks.
Source: HUMAN
Disrupting Scallywag
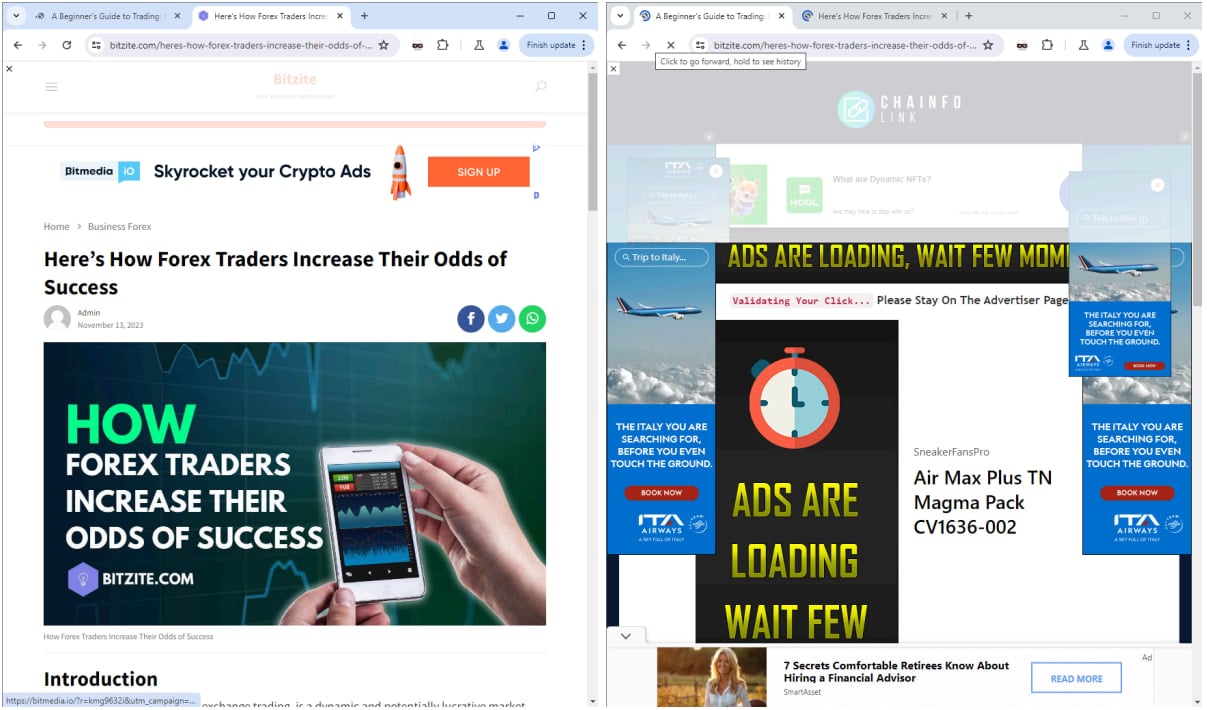
HUMAN detected Scallywag activity by analyzing traffic patterns across their partner network, such as high ad impression volume from seemingly benign WordPress blogs, cloaking behavior, and forced wait times or CAPTCHA interaction before redirection.
Source: HUMAN
Subsequently, it classified the network as fraudulent, working with ad providers to stop the bidding on ad requests and cutting Scallywag’s revenue stream.
In rsponse, the Scallywag actors tried to evade detection using new cashout domains and open redirect chains to hide the real referrer, but HUMAN says they detected and blocked those, too.
Source: HUMAN
As a result, Scallywag’s daily ad fraud traffic dropped sharply from 1.4 billion to nearly zero, with many affiliates abandoning the method and moving on to other scams.
Although the Scallywag ecosystem has economically collapsed, its operators will likely continue trying to evade the mitigations and return to profits.