.png
)









Introduction
Not all threats announce their presence. Some are designed for stealth, slipping through security measures with devastating effectiveness. In today’s digital workspace, understanding and identifying these threats before they cause irreparable damage is critical.
The Subtle Art of Malware Evasion
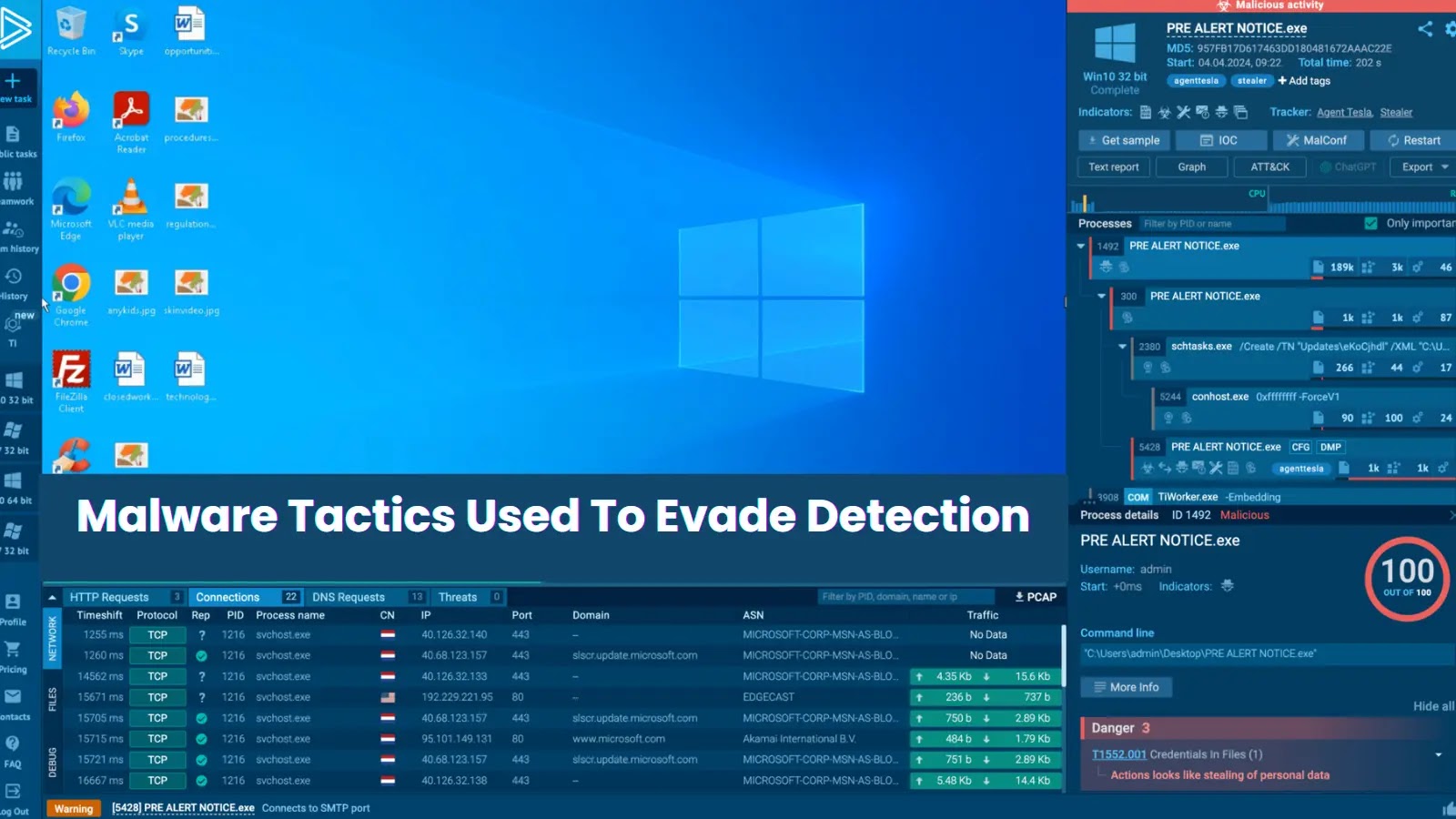
Modern cyber attackers are employing increasingly sophisticated methods to remain undetected within corporate environments. By understanding these tactics, your security team can enhance its defensive strategies and prevent potential breaches.
Overview of Stealth Techniques
The following are the top evasion methods that malware uses to infiltrate and operate within enterprise systems without detection:
- Extended dwell time that increases enterprise risk
- Blending malicious activities with normal network behavior
- Creating gaps in visibility that complicate the investigative process
- Undermining the trust in and effectiveness of detection tools
Despite these challenges, there are advanced security solutions capable of detecting these stealth techniques. For instance, using specialized sandbox environments helps reveal malicious operations by simulating how they would behave within a network.
Exploring the Top 5 Evasive Malware Tactics
Let’s dive deeper into the specific strategies cyber threats employ to dodge corporate cybersecurity measures:
1. Obfuscation and Social Engineering
Attackers often combine technical obfuscation with social engineering to trick users into executing malware themselves, which significantly reduces the chances of detection by automated systems. Real-life examples show that platforms like ANY.RUN can detect these tactics by monitoring sandbox activities and identifying abnormal behaviors in less than a minute.
2. Abuse of System Tools
Malware often misuses legitimate system tools to carry out malicious activities discreetly. One common tactic is the use of Regsvr32 to execute harmful scripts that appear benign to most antivirus solutions.
3. Stealthy Script Execution
Scripts can run invisibly via PowerShell with altered window styles or via VBScript with settings that avoid producing visible windows, allowing malware to operate undetected in the background.
4. Utilizing Legitimate Protocols and Services
Malware may mimic normal network traffic or hijack legitimate protocols, making it difficult for security tools to distinguish between benign and malicious activities.
5. Using Encrypted Channels for Command and Control
By communicating over encrypted connections, like HTTPS or custom protocols, attackers can prevent security tools from intercepting or analyzing malicious traffic.
Equip Your Team with the Right Tools
Knowing these tactics is only part of the battle. Equipping your security team with the ability to detect and respond to advanced threats swiftly is crucial. Sandbox environments like ANY.RUN provide a real-time view into how threats operate, empowering your team to act quickly and decisively.
Start a free trial of ANY.RUN and experience how it can help secure your enterprise against sophisticated cyber threats.
Related: Unlock the Secrets of Social Engineering: Essential Insights for Robust Organizational
Last Updated: April 16, 2025