An ongoing PayPal email scam exploits the platform’s address settings to send fake purchase notifications, tricking users into granting remote access to scammers
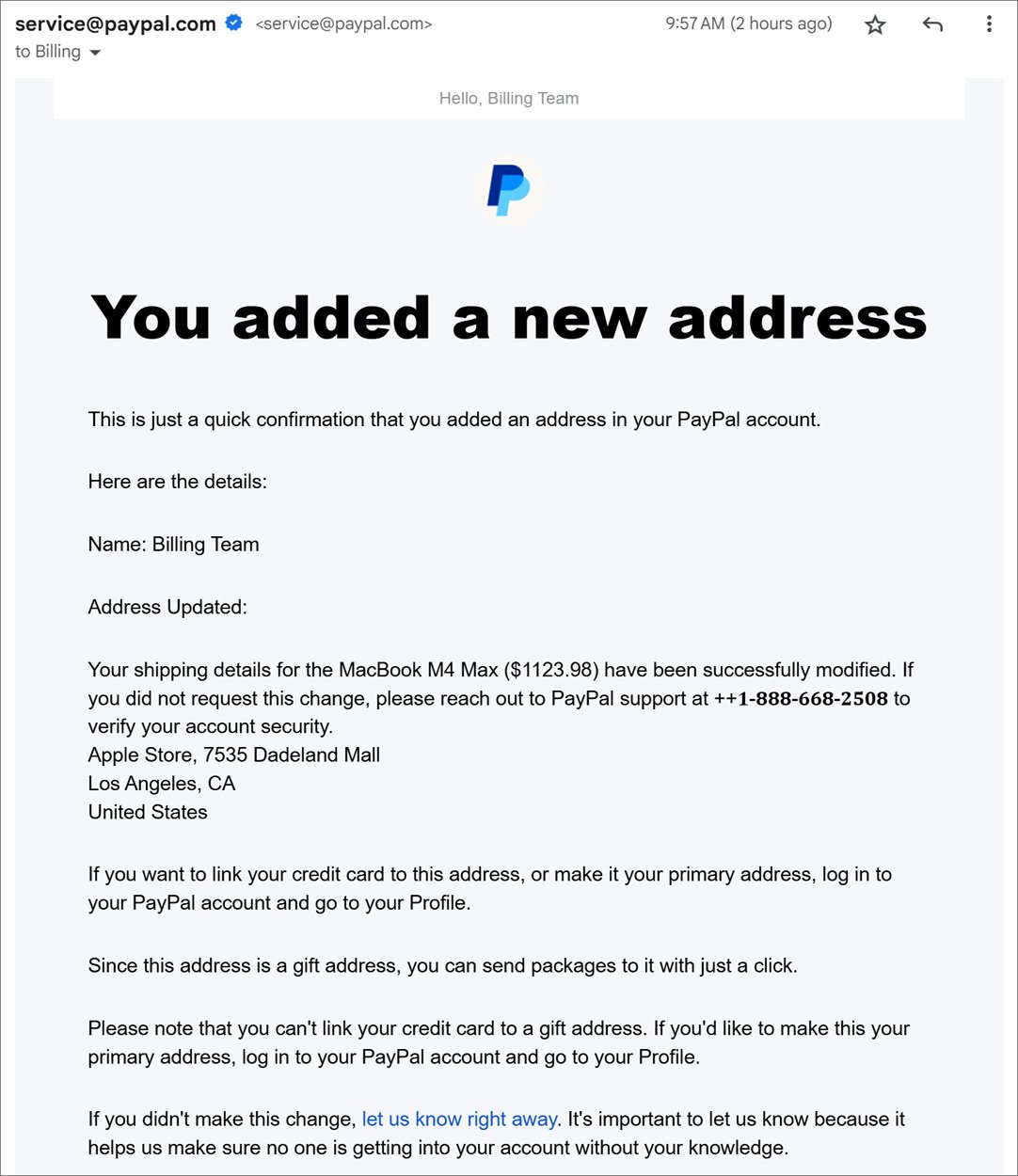
For the past month, BleepingComputer and others [1, 2] have received emails from PayPal stating, “You added a new address. This is just a quick confirmation that you added an address in your PayPal account.”
The email includes the new address that was allegedly added to your PayPal account, including a message claiming to be a purchase confirmation for a MacBook M4, and to call the enclosed PayPal number if you did not authorize the purchase.
“Confirmation: Your shipping address for the MacBook M4 Max 1 TB ($1098.95) has been changed. If you did not authorize this update, please reach out to PayPal at +1-888-668-2508′,” reads the scam email.
Source: BleepingComputer
The emails are being sent directly by PayPal from the address “service@paypal.com,” causing people to be concerned their account was hacked.
However, those who received this email confirmed that no new addresses were actually added to their accounts. In our case, the scam email was sent to an email address with no PayPal account.
Furthermore, as the emails are legitimate PayPal emails, they are bypassing security and spam filters. In the next section, we will explain how scammers send these emails.
The goal of these emails is to trick recipients into thinking their account was hacked to purchase a MacBook and scare the email recipient into calling the scammer’s “PayPal support” phone number.
When calling the number, a recording will automatically play stating that you have reached PayPal customer service and to hold while a support person becomes available. The call will then attempt to connect you to a “customer support” person.
This scammer will try to scare you into thinking your account was hacked and convince you to download and run the software so that they can “help” you regain access to the account and block the alleged transaction.
The scammer will direct you to visit a site like pplassist[.]com and enter a service code given by the fake PayPal employee. Entering this code will download a ConnectWise ScreenConnect client [VirusTotal] from lokermy.numaduliton[.]icu or other sites, which the scammer will ask you to run.
Source: BleepingComputer
At this point, we hung up on the scammer and did not execute the program on our devices.
However, in previous scams like this, once the threat actor gains access to the computer, they attempt to steal money from bank accounts, deploy malware, or steal data from the computer.
Therefore, if you receive a legitimate email from PayPal stating you updated your address, and it contains a bogus purchase confirmation, simply ignore the email and do not contact the listed phone number as it belongs to the scammer.
To be safe, instead, log into your PayPal account and confirm no additional addresses were added, and if not, junk the email.
How the PayPal scam works
When BleepingComputer first received this email, we were confused as the email was sent from “service@paypal.com” to an email address that does not have a PayPal account associated with it.
Furthermore, the mail headers show that the emails are legitimate, passing DKIM email security checks and originating directly from PayPal’s mail server, as shown below.
Received: from mx1.phx.paypal.com (mx1.phx.paypal.com. [66.211.170.87])
by mx.google.com with ESMTPS id 41be03b00d2f7-addf237d3e1si10521113a12.387.2025.02.18.07.30.09
for
It was unclear at first how these legitimate emails were being sent from PayPal until we noticed this text at the bottom of the email.
“If you want to link your credit card to this address, or make it your primary address, log in to your PayPal account and go to your Profile,” reads the PayPal email notification.
“Since this address is a gift address, you can send packages to it with just a click.”
Further research revealed that “gift addresses” are just additional addresses you can add to your PayPal profile.
In a test, BleepingComputer added a new address to one of our accounts and pasted the scammer’s fake MacBook purchase confirmation message into the Address 2 field.
After saving the address, PayPal sent us the same confirmation email, notifying us of the new address we added, which also included the fake purchase message.
Now that we know how they are generating the email from PayPal, we still do not know how they are getting PayPal to send it to all of the targets.
Upon further analysis of the mail headers, we can see that the email is actually being sent to the address “noreply_@usaea.institute,” which is the email address associated with the scammer’s PayPal address.
The headers further show that this email address automatically forwards the email it receives to “bill_complete1@zodu.onmicrosoft.com”, an account associated with a Microsoft 365 tenant.
This account is likely a mailing list, which automatically forwards any email it receives to all other group members. In this case, the members are you and I, the scammer’s targets.
When they add the scam address to PayPal, the payment platform will email a confirmation to the threat actor’s email, which will then forward it to the Microsoft 365 account, which then forwards it to everyone on the mailing list, as shown in the flow chart below.
Source: BleepingComputer
PayPal enables this scam by not limiting the number of characters in the address form fields, allowing the threat actors to inject their scam message.
To fix this, PayPal needs to restrict the number of characters in the address field to a reasonable character count, like 50 characters, if not less.
BleepingComputer contacted PayPal about this scam and is awaiting a response to our email.
