Introducing Enhanced Endpoint Containment
Microsoft is currently piloting a novel capability within its Defender for Endpoint security solution, aimed at enhancing network security. This function will effectively block both inbound and outbound traffic to unknown endpoints, curbing the chances of attackers moving laterally across the network.
How It Works
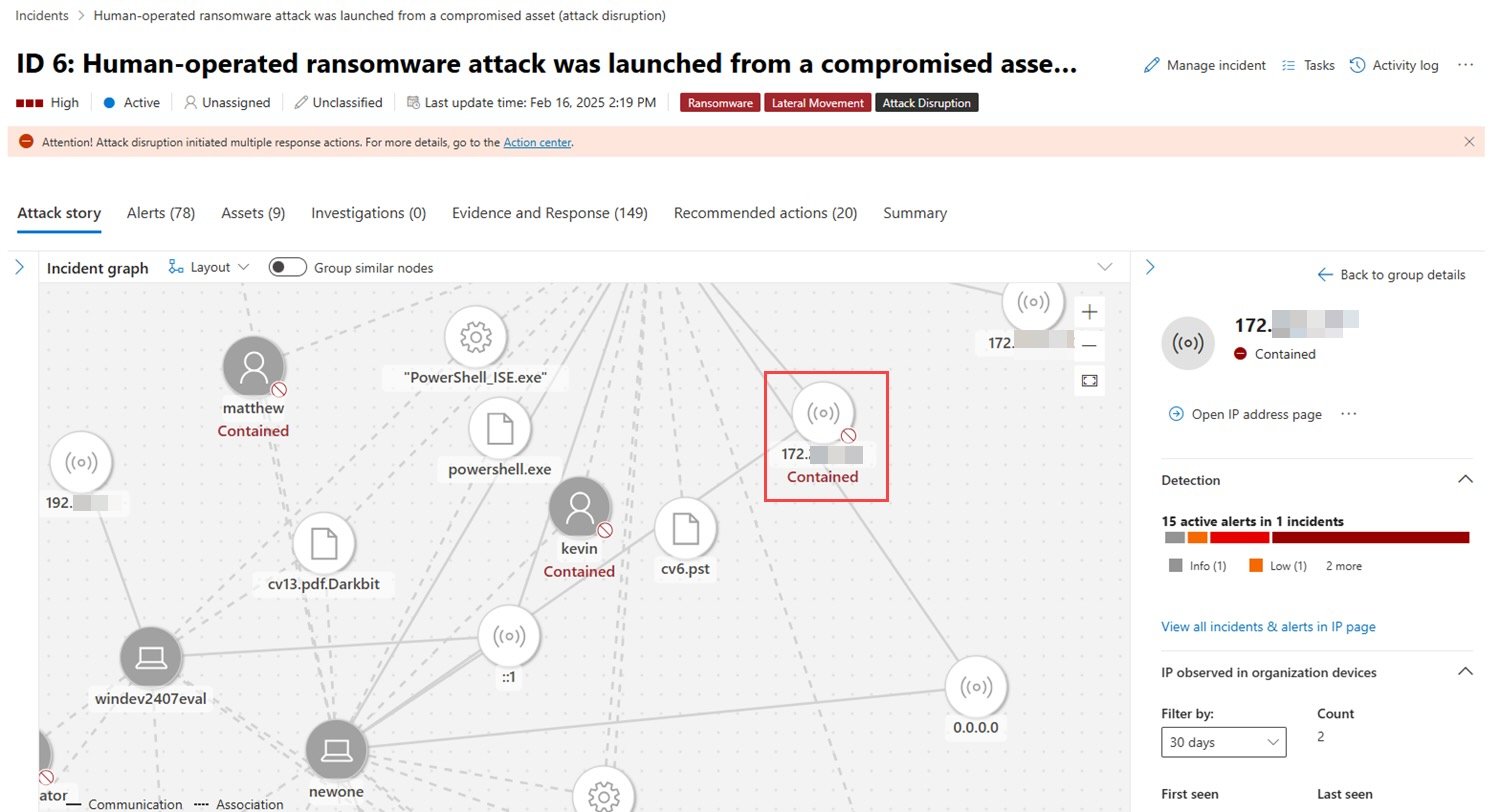
This security advancement functions by isolating the IP addresses of devices that have not been registered or integrated into the Defender for Endpoint system. As Microsoft announced, this process automatically flags and blocks the communication of these IP addresses, thereby preventing threat actors from leveraging them to compromise additional network devices.
Automated Attack Disruption
The containment of IP addresses is managed through Defender for Endpoint’s automatic attack disruption feature. When an IP is detected as belonging to an unregistered device, the system triggers a containment policy which blocks the IP, ensuring that threat actors cannot use it as a pivot point in their attack chain.
The policy applies stringent controls including the selective blocking of specific ports and directions of communication, aimed at containing the threat without disrupting normal network operations.
Availability and Control
The new feature is set to be available for devices onboarded on Defender for Endpoint running on a variety of platforms including Windows 10, Windows Server 2012 R2, and newer versions. Network administrators have the flexibility to manage IP containments, including the ability to restore connections quickly via the “Action Center” by simply selecting the “Undo” option.
Past and Ongoing Improvements
Defender for Endpoint has continuously expanded its capabilities. Since June 2022, it has enabled the isolation of compromised Windows devices, effectively stopping malicious communications and preventing further infiltration. As of October 2023, this isolation feature has also been integrated for macOS and Linux systems.
In the same stride, new functionalities for tackling compromised user accounts were introduced, enhancing defenses against ransomware and other hands-on-keyboard attacks.
Additional Resources and Insights
Explore in-depth analytics and preventative techniques available in the latest industry reports, detailing how to counter predominant cyber threats effectively.
Related: Unlock New Productivity with Windows Recall: Your Essential Guide to the Latest
Last Updated: April 11, 2025




