A North Korean threat group has been using a technique called RID hijacking that tricks Windows into treating a low-privileged account as one with administrator permissions.
The hackers used a custom malicious file and an open source tool for the hijacking attack. Both utilities can perform the attack but researchers at South Korean cybersecurity company AhnLab say that there are differences.
How RID hijacking works
The Relative Identifier (RID) in Windows is part of the Security Identifier (SID), a unique tag assigned to every user account to distinguish between them.
RID can take values that indicate the account’s level of access, such as “500” for administrators, “501” for guest accounts, “1000” for regular users, and “512” for the domain admins group.
RID hijacking occurs when attackers modify the RID of a low-privilege account to match the value of an administrator account, and Windows will grant it elevated access.
However, performing the attack requires access to the SAM registry, so the hackers need to first breach the system and gain SYSTEM access.
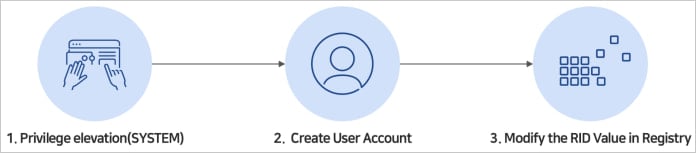
Source: ASEC
Andariel attacks
ASEC researchers, AhnLab’s security intelligence center, attribute the attack to Andariel threat group, which has been linked to North Korea’s Lazarus hacker group.
The attacks begin with Andariel having SYSTEM access on the target via the exploitation of a vulnerability.
The hackers achieve the initial escalation by using tools such as PsExec and JuicyPotato to launch a SYSTEM-level command prompt.
Although SYSTEM access is the highest level on Windows, it does not allow remote access, cannot interact with GUI apps, is very noisy and likely to be detected, and cannot persist between system reboots.
To address these issues, Andariel first created a hidden, low-privilege local user by using the “net user” command and adding the ‘$’ character at the end.
In doing so, the attacker ensured that the account is not visible through the “net user” command and can be identified only in the SAM registry. Then they performed the RID hijacking to increase permissions to admin.
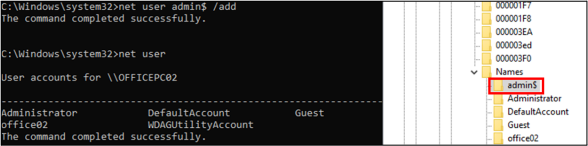
source: AhnLab
According to the researchers, Andariel added their account to the Remote Desktop Users and Administrators groups.
The RID hijacking required for this is possible through Security Account Manager (SAM) registry modifications. The North Koreans use custom malware and an open-source tool to perform the changes.
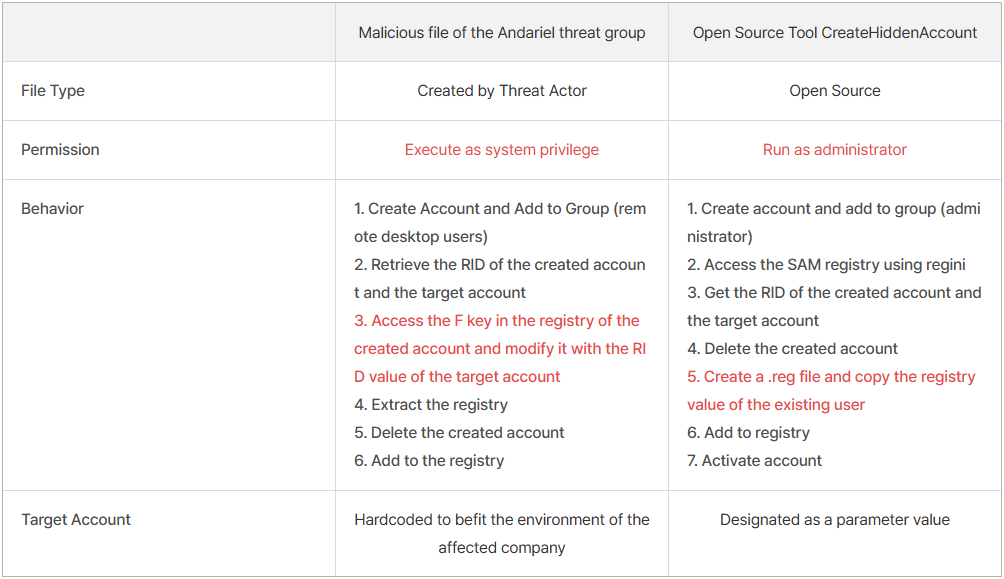
Although SYSTEM access allows admin account creation directly, certain restrictions may apply depending on the security settings. Elevating the privileges of regular accounts is far stealthier and harder to detect and stop.
Andariel further attempts to cover its tracks by exporting the modified registry settings, deleting the key and the rogue account, and then re-registering it from a saved backup, allowing reactivation without appearing in system logs.
To mitigate risks for RID hijacking attacks, system admins should use Local Security Authority (LSA) Subsystem Service to check for logon attempts and password changes, as well as prevent unauthorized access and changes to the SAM registry.
It is also advisable to restrict the execution of PsExec, JuicyPotato, and similar tools, disable the Guest account, and protect all existing accounts, even low-privileged, with multi-factor authentication.
It is worth noting that RID hijacking has been known since at least 2018 when security researcher Sebastián Castro presented the attack at DerbyCon 8 as a persistence technique on Windows systems.




