Hackers are believed to be exploiting recently fixed SimpleHelp Remote Monitoring and Management (RMM) software vulnerabilities to gain initial access to target networks.
The flaws, tracked as CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728, allow threat actors to download and upload files on devices and escalate privileges to administrative levels.
The vulnerabilities were discovered and disclosed by Horizon3 researchers two weeks ago. SimpleHelp released fixes between January 8 and 13 in product versions 5.5.8, 5.4.10, and 5.3.9.
Arctic Wolf now reports about an ongoing campaign targeting SimpleHelp servers that started roughly a week after Horizon3’s public disclosure of the flaws.
The security company isn’t 100% certain that the attacks leverage these flaws but connects its observations to Horizon3’s report with medium confidence.
“While it is not confirmed that the recently disclosed vulnerabilities are responsible for the observed campaign, Arctic Wolf strongly recommends upgrading to the latest available fixed versions of the SimpleHelp server software where possible,” reads the report.
“In situations where the SimpleHelp client was previously installed on devices for third-party support sessions but isn’t actively being used for day-to-day operations, Arctic Wolf recommends uninstalling the software to reduce the potential attack surface.”
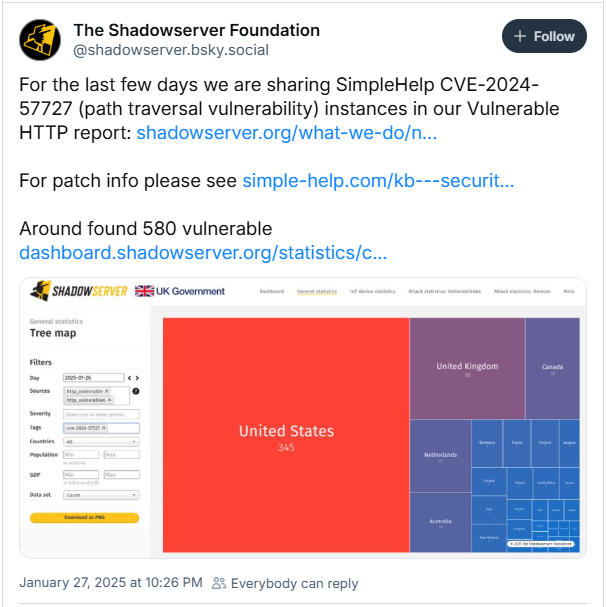
Threat monitoring platform Shadowserver Foundation reported they see 580 vulnerable instances exposed online, most (345) located in the United States.
Attacks in the wild
Artic Wolf reports that the SimpleHelp ‘Remote Access.exe’ process was already running in the background before the attack, indicating that SimpleHelp was previously installed for remote support sessions on the devices.
The first sign of compromise was the SimpleHelp client on the target device communicating with an unapproved SimpleHelp server.
This is possible by either the attacker exploiting flaws in SimpleHelp to gain control of the client or using stolen credentials to hijack the connection.
Once inside, the attackers ran cmd.exe commands like ‘net’ and ‘nltest’ to gather intelligence about the system, including a list of user accounts, groups, shared resources, and domain controllers, and test Active Directory’s connectivity.
These are common steps before performing privilege escalation and lateral movement. However, Arctic Wolf says the malicious session was cut off before it could be determined what the threat actor would do next.
SimpleHelp users are recommended to upgrade to the latest version that addresses the CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728 flaws.
More information about how to apply the security updates and verify the patch is available in SimpleHelp’s bulletin.
If SimpleHelp clients were installed in the past to accommodate remote support sessions but are no longer needed, it would be best that they be uninstalled from the systems to eliminate the attack surface.