Scammers are impersonating the BianLian ransomware gang in fake ransom notes sent to US companies via snail mail through the United States Postal Service.
The fake ransom notes were first reported by Guidepoint Security today, with BleepingComputer later being sent a scan of the note from a CEO who received the same letter.
The envelopes for these ransom notes claim to be from the “BIANLIAN Group” and have a return address located in an office building in Boston, Massachusets:
BIANLIAN GROUP
24 FEDERAL ST, SUITE 100
BOSTON, MA 02110
In the letter shared with BleepingComputer, the envelope shows it was mailed on February 25th, 2025. This mailing date is the same as the one seen by Arctic Wolf, who also reported on the scam today.
The letters are being mailed to the CEO of the companies at their corporate mailing address and show that they were processed through a postal facility in Boston, with the envelope marked, “Time Sensitive Read Immediately.”

Source: BleepingComputer
The envelopes contain a ransom note addressed to the company’s CEO or another executive, claiming to be from the BianLian ransomware operation. According to notes reviewed by BleepingComputer, they are tailored to the company’s industry, with different types of allegedly stolen data corresponding to the company’s activities.
For example, fake BianLian ransom notes sent to healthcare companies claim that patient and employee information was stolen, while those targeting product-based businesses allege the exposure of customer orders and employee data.
“I regret to inform you that we have gained access to [REDACTED] systems and over the past several weeks have exported thousands of data files, including customer order and contact information, employee information with IDs, SSNs, payroll reports, and other sensitive HR documents, company financial documents, legal documents, investor and shareholder information, invoices, and tax documents,” reads a fake BianLian ransom note.
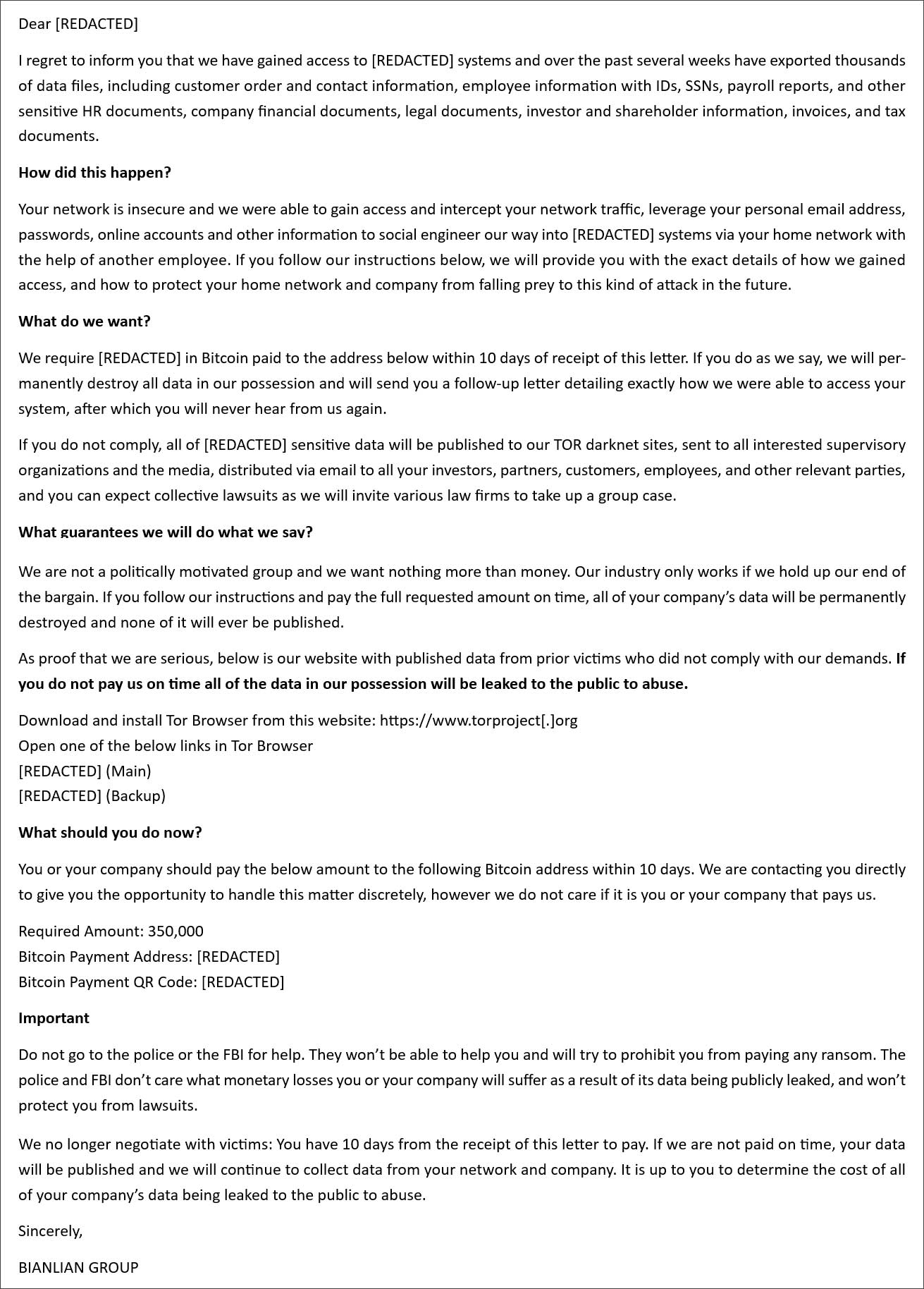
Source: GuidePoint Security
The mailed ransom notes are very different from BianLian’s, but the scammers attempt to make them look convincing by including the real Tor data leak sites for the ransomware operation in the notes.
However, unlike typical ransomware demands, these fake notes state that BianLian is no longer negotiating with victims. Instead, the victim has 10 days to make a Bitcoin payment to prevent data from being leaked.
Each ransom note includes a ransom demand ranging between $250,000 and $500,000, a freshly generated Bitcoin address to send payment, and a QR code for the Bitcoin address.
Arctic Wolf said that all healthcare organizations had their ransom demand set to $350,000, which is the same as the one shared by a healthcare company with BleepingComputer, as shown below.
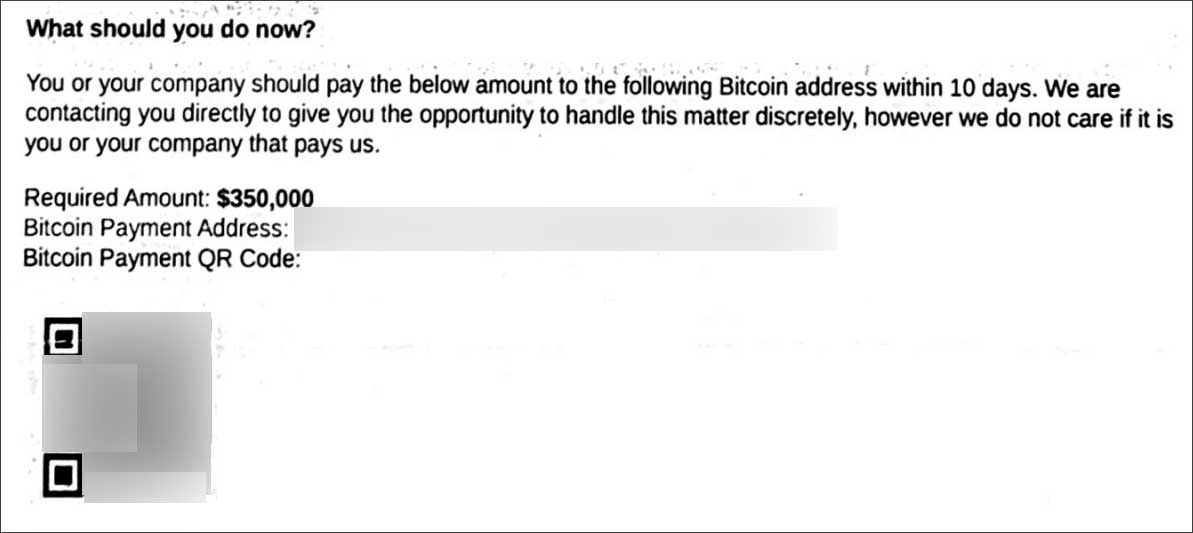
Source: BleepingComputer
Furthermore, Arctic Wolf states that two ransom notes the researchers saw included legitimate compromised passwords to add legitimacy to the demand.
“In at least two letters, the threat actor included a compromised password within the How did this happen? section, almost certainly in an attempt to add legitimacy to their claim.” explained Arctic Wolf.
The consensus in the reports is that these ransom notes are fake and are only designed to scare executives into paying a ransom, as there are no signs of an actual breach.
“While GRIT cannot confirm the identity of the letter’s authors at this time, we assess with a high level of confidence that the extortion demands contained within are illegitimate and do not originate from the BianLian ransomware group,” explains GuidePoint Security researcher Grayson North.
However, this does not mean the emails should be ignored. Due to the widespread mailing of these notes, all IT and security admins should notify executives about the scam so that they are aware and do not waste time and resources worrying about them.
These fake ransom notes are an evolution of the email extortion scams that have become so popular since 2018. However, instead of targeting personal emails, they are now targeting the CEOs of corporations.
BleepingComputer contacted the BianLian ransomware operation to see if they were involved with these mailings, but a reply was not immediately available.




