
Overview of the Incident
The dark web leak site operated by the notorious Everest ransomware gang was compromised and taken offline after an attack by an unidentified intruder this past weekend. Reports suggest that the site is now inaccessible, displaying an “Onion site not found” error, indicating the removal of the platform by the Everest group.
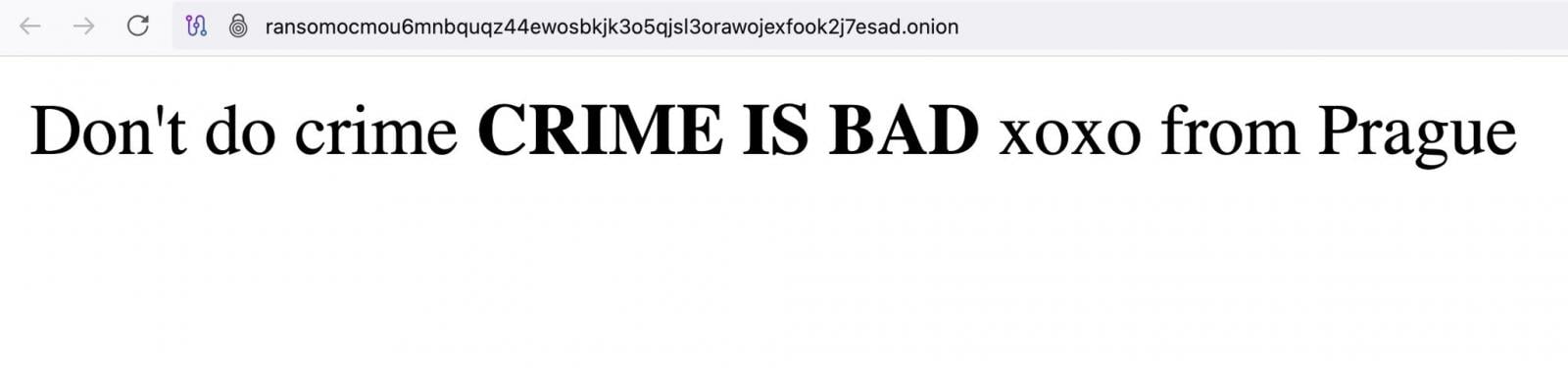
Sarcastic Message Replaces Homepage Content
During the attack, the intruder substituted the homepage content with a mocking message: “Don’t do crime CRIME IS BAD xoxo from Prague,” leaving a stark reminder of the vulnerability even among cybercriminal circles.
Possible Exploit Leads to Security Breach
Security experts, including Flare Senior Threat Intelligence Researcher Tammy Harper, speculate that a WordPress vulnerability might have facilitated the unauthorized access to Everest’s leak site. Harper highlighted the group’s use of a WordPress template which could have been the breach point. This incident sheds light on the critical importance of securing web infrastructure, even for cybercriminal groups.
The Evolution of Everest Ransomware Operations
Since its emergence in 2020, Everest has expanded its criminal repertoire. Initially focusing only on data theft for corporate extortion, it has now incorporated ransomware into its attacks to encrypt victims’ data and intensify its extortion tactics. The operators also act as initial access brokers, selling entry points into compromised corporate networks to other cybercriminal entities.
Impact and Extortion Tactics
Over the past five years, more than 230 victims have been listed on Everest’s dark web site as part of its double-extortion scheme—threatening the release of sensitive files to manipulate victims into paying ransoms:
- STIIIZY, a well-known cannabis brand based in California, became one of Everest’s claimed victims in November 2024.
- In January, it was revealed that STIIIZY’s point-of-sale (POS) vendor had been compromised, leading to significant data breaches, including the leakage of customer purchase details and government IDs.
- Everest’s targeting spree has recently included U.S. healthcare organizations, as confirmed by an August 2024 warning from the U.S. Department of Health and Human Services.
Conclusion: A Stark Reminder of Ongoing Cyber Threats
This defacement and subsequent offline status of the Everest ransomware leak site act as a poignant reminder of the persistent threats and vulnerabilities existing within digital environments—impacting criminals and legitimate entities alike. It underscores the continual need for robust cybersecurity measures across all sectors.
Related: Google Enhances Android Security by Patching 62 Vulnerabilities, Including Crucial
Last Updated: April 7, 2025




