The FBI is warning that the BADBOX 2.0 malware campaign has infected over 1 million home Internet-connected devices, converting consumer electronics into residential proxies that are used for malicious activity.
The BADBOX botnet is commonly found on Chinese Android-based smart TVs, streaming boxes, projectors, tablets, and other Internet of Things (IoT) devices.
“The BADBOX 2.0 botnet consists of millions of infected devices and maintains numerous backdoors to proxy services that cyber criminal actors exploit by either selling or providing free access to compromised home networks to be used for various criminal activity,” warns the FBI.
These devices come preloaded with the BADBOX 2.0 malware botnet or become infected after installing firmware updates and through malicious Android applications that sneak onto Google Play and third-party app stores.
“Cyber criminals gain unauthorized access to home networks by either configuring the product with malicious software prior to the users purchase or infecting the device as it downloads required applications that contain backdoors, usually during the set-up process,” explains the FBI.
“Once these compromised IoT devices are connected to home networks, the infected devices are susceptible to becoming part of the BADBOX 2.0 botnet and residential proxy services4 known to be used for malicious activity.”
Once infected, the devices connect to the attacker’s command and control (C2) servers, where they receive commands to execute on the compromised devices, such as:
- Residential Proxy Networks: The malware routes traffic from other cybercriminals through victims’ home IP addresses, masking malicious activity.
- Ad Fraud: BADBOX can load and click ads in the background, generating ad revenue for the threat actors.
- Credential Stuffing: By leveraging victim IPs, attackers attempt to access other people’s accounts using stolen credentials.
BADBOX 2.0 evolved from the original BADBOX malware, which was first identified in 2023 after it was found pre-installed in cheap, no-name Android TV boxes like the T95.
Over the years, the malware botnet continued expanding until 2024, when Germany’s cybersecurity agency disrupted the botnet in the country by sinkholing the communication between infected devices and the attacker’s infrastructure, effectively rendering the malware useless.
However, that did not stop the threat actors, with researchers saying they found the malware installed on 192,000 devices a week later. Even more concerning, the malware was found on more mainstream brands, like Yandex TVs and Hisense smartphones.
Unfortunately, despite the previous disruption, the botnet continued to grow, with HUMAN’s Satori Threat Intelligence stating that over 1 million consumer devices had become infected by March 2025.
This new larger botnet is now being called BADBOX 2.0 to indicate a new tracking of the malware campaign.
“This scheme impacted more than 1 million consumer devices. Devices connected to the BADBOX 2.0 operation included lower-price-point, “off brand”, uncertified tablets, connected TV (CTV) boxes, digital projectors, and more,” explains HUMAN.
“The infected devices are Android Open Source Project devices, not Android TV OS devices or Play Protect certified Android devices. All of these devices are manufactured in mainland China and shipped globally; indeed, HUMAN observed BADBOX 2.0-associated traffic from 222 countries and territories worldwide.”
Researchers at HUMAN estimate that the BADBOX 2.0 botnet spans 222 countries, with the highest number of compromised devices in Brazil (37.6%), the United States (18.2%), Mexico (6.3%), and Argentina (5.3%).
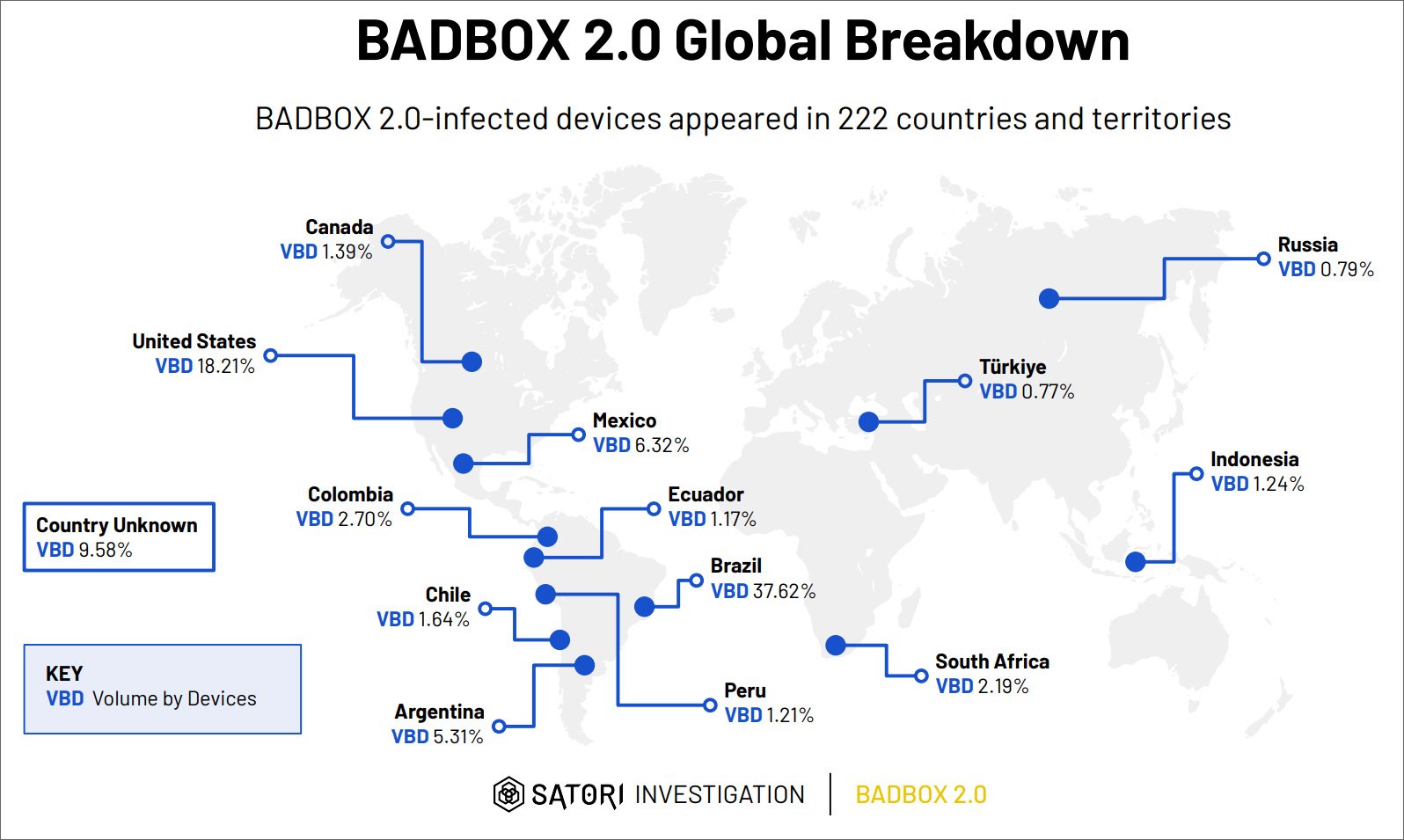
Source: HUMAN Satori
In a joint operation led by HUMAN’s Satori team and Google, Trend Micro, The Shadowserver Foundation, and other partners, the BADBOX 2.0 botnet was disrupted again to prevent over 500,000 infected devices from communicating with the attacker’s servers.
However, even with that disruption, the botnet continues to grow as consumers purchase more compromised products and connect them to the Internet.
A list of devices known to be impacted by the BADBOX malware are listed below:
| Device Model | Device Model | Device Model | Device Model |
| TV98 | X96Q_Max_P | Q96L2 | X96Q2 |
| X96mini | S168 | ums512_1h10_Natv | X96_S400 |
| X96mini_RP | TX3mini | HY-001 | MX10PRO |
| X96mini_Plus1 | LongTV_GN7501E | Xtv77 | NETBOX_B68 |
| X96Q_PR01 | AV-M9 | ADT-3 | OCBN |
| X96MATE_PLUS | KM1 | X96Q_PRO | Projector_T6P |
| X96QPRO-TM | sp7731e_1h10_native | M8SPROW | TV008 |
| X96Mini_5G | Q96MAX | Orbsmart_TR43 | Z6 |
| TVBOX | Smart | KM9PRO | A15 |
| Transpeed | KM7 | iSinbox | I96 |
| SMART_TV | Fujicom-SmartTV | MXQ9PRO | MBOX |
| X96Q | isinbox | Mbox | R11 |
| GameBox | KM6 | X96Max_Plus2 | TV007 |
| Q9 Stick | SP7731E | H6 | X88 |
| X98K | TXCZ |
Symptoms of a BADBOX 2.0 infection include suspicious app marketplaces, disabled Google Play Protect settings, TV streaming devices advertised as being unlocked or able to access free content, devices from unknown brands, and suspicious Internet traffic.
Furthermore, this malware is commonly found on devices not Google Play Protect certified.
The FBI strongly advises consumers to protect themselves from the botnet by following these steps:
- Assess all IoT devices connected to home networks for suspicious activity.
- Never download apps from unofficial marketplaces offering “free streaming” apps.
- Monitor Internet traffic to and from home networks.
- Keep all devices in your home updated with the latest patches and updates.
Finally, if you suspect your device is compromised, you should isolate it from the rest of the network and restrict its Internet access, effectively disrupting the malware.





