As cyberattacks grow more sophisticated, hackers are increasingly utilizing legitimate credentials to bypass security defenses, making credential-based breaches a top threat for organizations worldwide. A staggering 47% of cloud breaches involve weak or stolen credentials, highlighting an urgent need for robust security practices.
Understanding the Preference for Credential-Based Attacks
Hackers favor credential-based methods for several compelling reasons:
- Simple execution: These attacks require fewer resources than sophisticated exploits, yet are incredibly effective.
- High success rate: Common password reuse across accounts makes it easier for attackers to gain widespread access.
- Low detection risk: Using legitimate credentials allows attackers to remain undetected, blending in with normal user activity.
- Cost-effectiveness: Attackers can purchase stolen credentials at low costs and use automated tools to test their validity across platforms.
- Versatility: Credential-based attacks can be deployed across any entry point that requires login information, from enterprise networks to cloud services.
Why Your Organization Might Be Targeted
Organizations with specific weaknesses are prime targets for these attacks:
- Inadequate password policies that allow for simple password cracking.
- Lack of multi-factor authentication, leaving even strong passwords vulnerable.
- Poor employee training on cybersecurity risks like phishing and social engineering.
- Deficient network segmentation that allows extensive access through a single point of compromise.
- Insufficient monitoring that fails to detect unusual activities quickly.
Immediate Action Steps Upon Credential Compromise
When an attack is detected, the response time is critical. Here are the essential steps an organization should take:
- Initial detection and alerting: Swift actions are crucial as soon as an anomaly is detected to mitigate damage.
- Assessment and triage: Confirm the breach and identify the affected systems and scope of impact.
- Isolation and containment: Limit further access by disconnecting affected systems and modifying access controls.
- Detailed forensic investigation: Track the incident’s origin and methods to better secure vulnerabilities.
- Transparent communication: Maintain trust by updating all stakeholders with accurate and timely information.
- Eradication and recovery: Strengthen security postures by resetting compromised credentials and repairing vulnerabilities.
- Post-incident review: Evaluate the incident response and strengthen defense mechanisms to prevent future incidents.
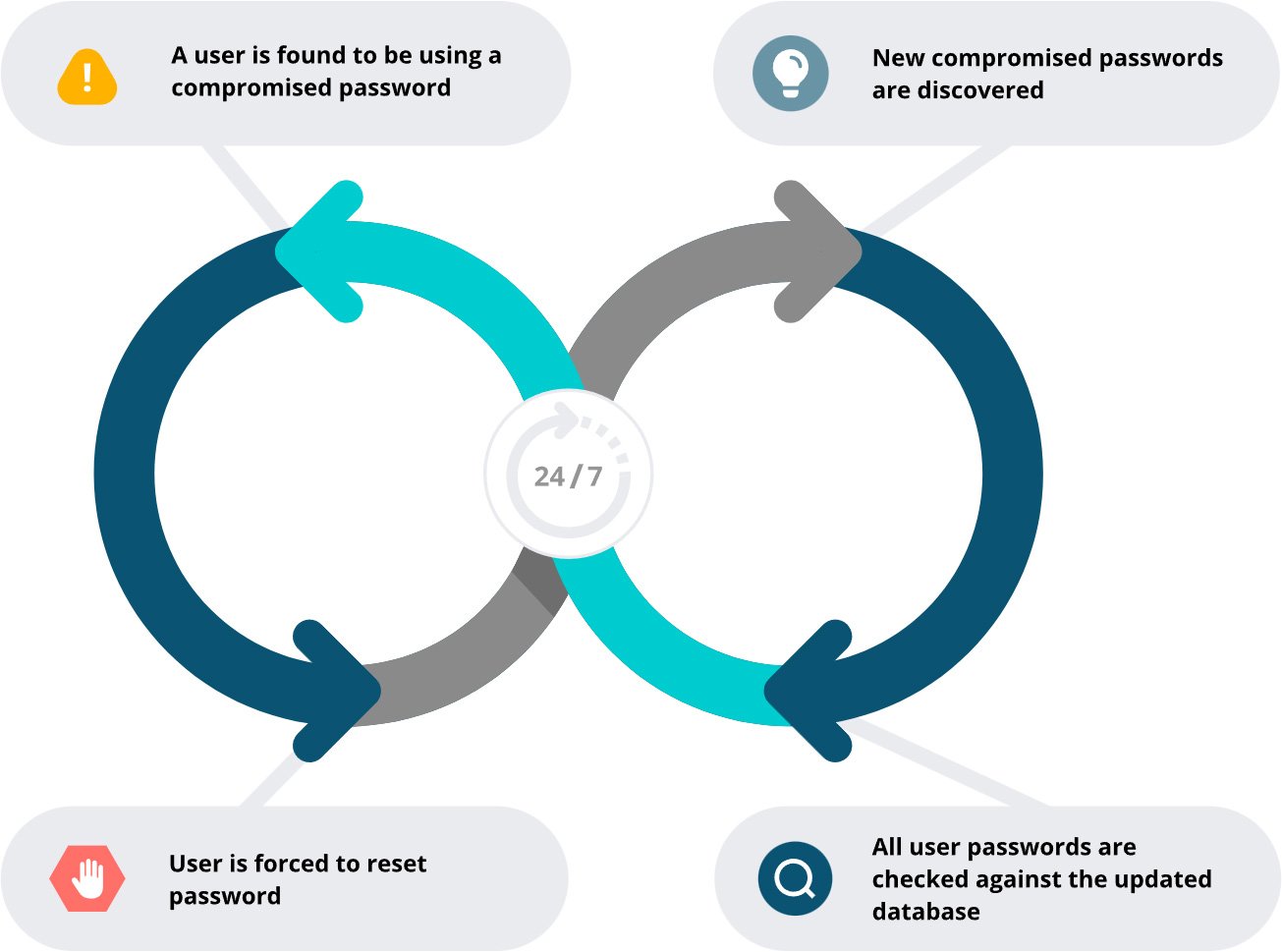
Proactive Measures: Scanning Active Directory
Preventing credential-based attacks begins with proactive security practices. Regularly auditing Active Directory and enforcing strong password policies reduce the risks of compromised credentials. Advanced tools like Specops Password Policy enhance security by scanning directories against extensive databases of known compromised passwords, prompting immediate updates to exposed passwords.
By adopting comprehensive, proactive security measures, your organization can defend against the infiltration strategies preferred by modern cybercriminals. Try Specops Password Policy for free today to elevate your cybersecurity readiness.
Related: 5 Shocking Ways Chinese Hackers Employ Upgraded RAT Malware Against Russia
Last Updated: April 18, 2025




