Introduction to Precision-Validated Phishing
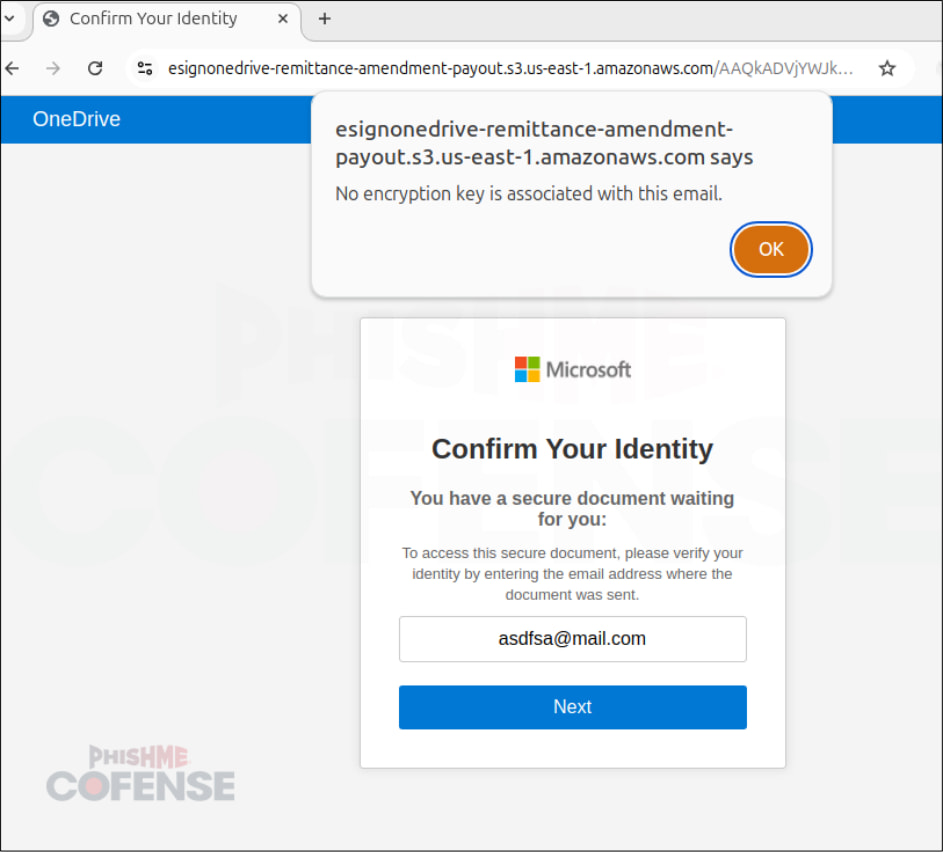
Phishing attackers have developed a sophisticated method known as Precision-Validated Phishing. This technique cleverly displays fraudulent login forms only when specific, high-value email addresses are entered by users, intensifying the threat to targeted individuals.
How It Works: The Rise of Target-Specific Phishing
Contrary to the scattergun approach traditionally associated with phishing, this refined technique leverages real-time email validation to ensure that only pre-selected, valuable targets are presented with phishing content. This focused method not only enhances the effectiveness of the attacks but also shields the phishing operations from unwanted scrutiny.
Impact on Cybersecurity Research
Cybersecurity firms, like Cofense, face new challenges due to this tactic. Researchers who typically insert control or fake email addresses to trace and analyze phishing networks are thwarted. Inputs by researchers now result either in errors or redirections to harmless websites, thereby concealing the malicious activity and extending the campaigns’ operational lifespan.
Advanced Evasion Techniques
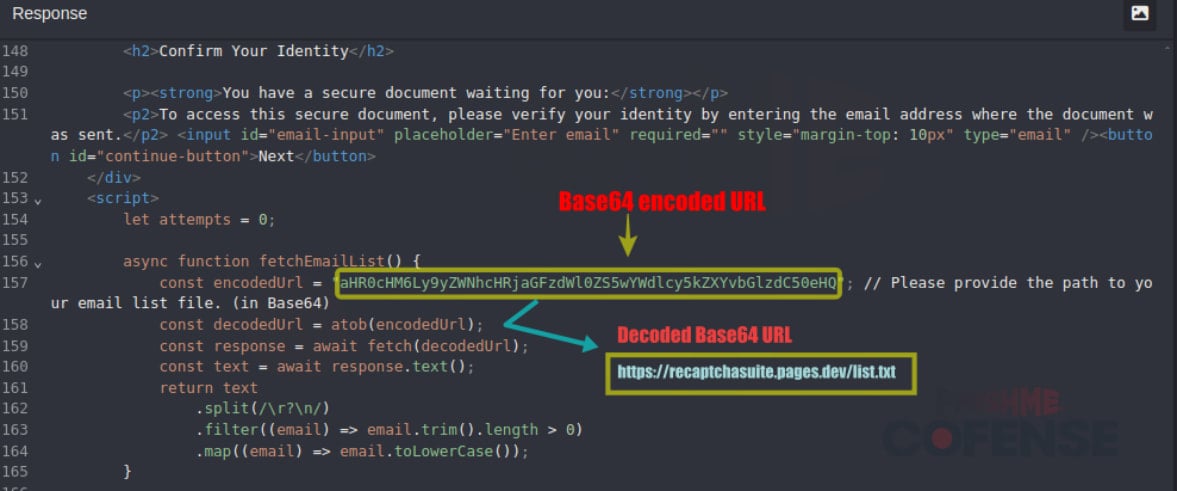
The attackers utilize innovative methods to implement real-time email checks. These include:
- Abusing third-party email verification services to authenticate email addresses instantly through API
- Deploying custom JavaScript that verifies whether an email is on the attackers’ pre-determined list of targets by communicating with their server
If the email is not recognized, the would-be victim is redirected to an innocuous page, preventing any malicious action.
Strategies to Counter Sophisticated Phishing Attacks
Phishing campaigns are becoming more adept at avoiding detection through dynamic input validation. As such, defenders are compelled to develop new strategies that prioritize behavioral analysis, and exploit real-time threat intelligence to effectively counter these precisely-targeted phishing operations.
Severe Implications for Email Security Tools
Traditional detection tools are increasingly inadequate against these sophisticated phishing tactics, highlighting an urgent need for innovation in cybersecurity defenses to protect against evolving threats.
Conclusion
As phishing techniques become more refined, it is crucial for cybersecurity professionals to remain vigilant and innovate continuously. Emphasizing advanced detection methods and adapting to the cunning nature of modern cyber threats is essential to safeguard valuable digital assets.
Related: Global Crackdown on Cybercrime: Authorities Detain Smokeloader Malware Affiliates and
Last Updated: April 9, 2025




