
Overview of the Threat
Cyber criminals are exploiting SourceForge, a well-respected software distribution platform, to push malicious Microsoft Office add-ins. These fraudulent tools compromise users’ systems to mine and steal cryptocurrency.
Understanding SourceForge’s Role
While SourceForge.net supports crucial development activities like version control and bug tracking, its openness has left it vulnerable to misuse. Even though it’s rare, this platform has become a channel for distributing malware.
The Impact So Far
A recent investigation by Kaspersky revealed that this malicious campaign has already affected over 4,604 devices, primarily in Russia, illustrating the significant reach and impact of these deceptive practices.
The Fake Office Add-Ins
The project dubbed officepackage mimics legitimate Microsoft developmental tools, specifically the ‘Office-Addin-Scripts’ from GitHub, to trick users. This deceit extends to search engine results, where searches for office add-ins misleadingly direct users to the compromised SourceForge project page.
How the Malware Operates
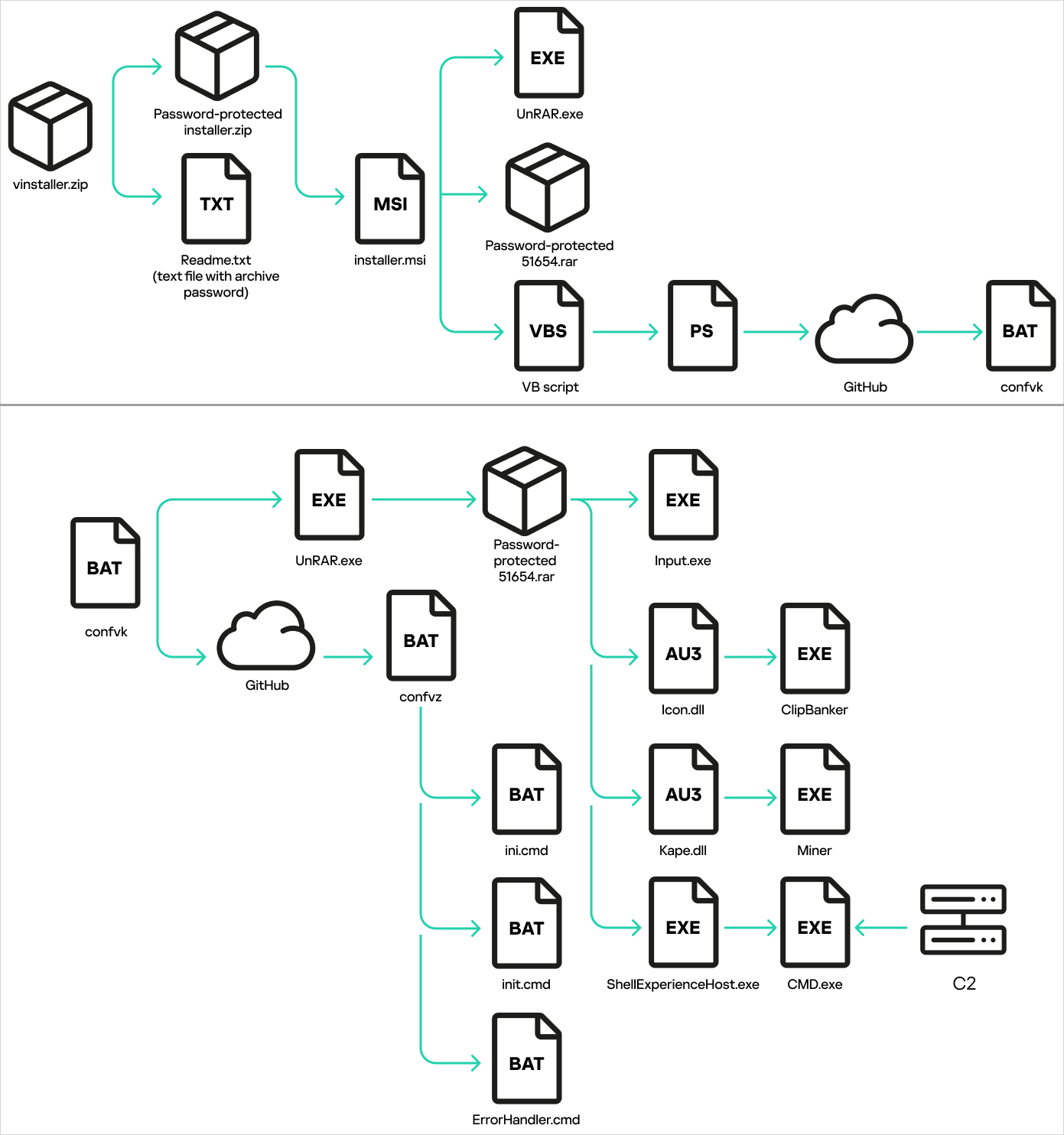
When unsuspecting users download from these fake pages, they receive a ZIP file containing a malicious MSI installer designed to evade antivirus detection by inflating its size to 700MB. Upon execution, this installer deploys a series of scripts and modifications:
- Initial Execution: A Visual Basic script fetches additional malicious scripts from GitHub.
- Persistence: Registry modifications and the addition of Windows services help maintain the malware’s presence.
- Dangerous Payloads:: Inclusion of a cryptocurrency miner and a clipper, the latter altering clipboard data to reroute cryptocurrency transactions to attacker-controlled wallets.
Protective Measures for Users
To avoid falling victim to such sophisticated attacks, users are advised to:
- Verify Publishers: Only download software from known and trusted sources, and verify the legitimacy of the developer.
- Use Official Channels: Prefer official project repositories over third-party sites, such as GitHub for Microsoft Office add-in scripts.
- Scan Downloads: Always use updated antivirus tools to scan all downloaded software before installation.
Conclusion
This campaign highlights the ongoing challenges in software distribution platforms, stressing the need for vigilance among developers and users alike to protect against these malicious exploits.
Related: Essential Fix Released for Kerberos Auth Problems in Windows 11 and Windows Server
Last Updated: April 8, 2025




