Introduction
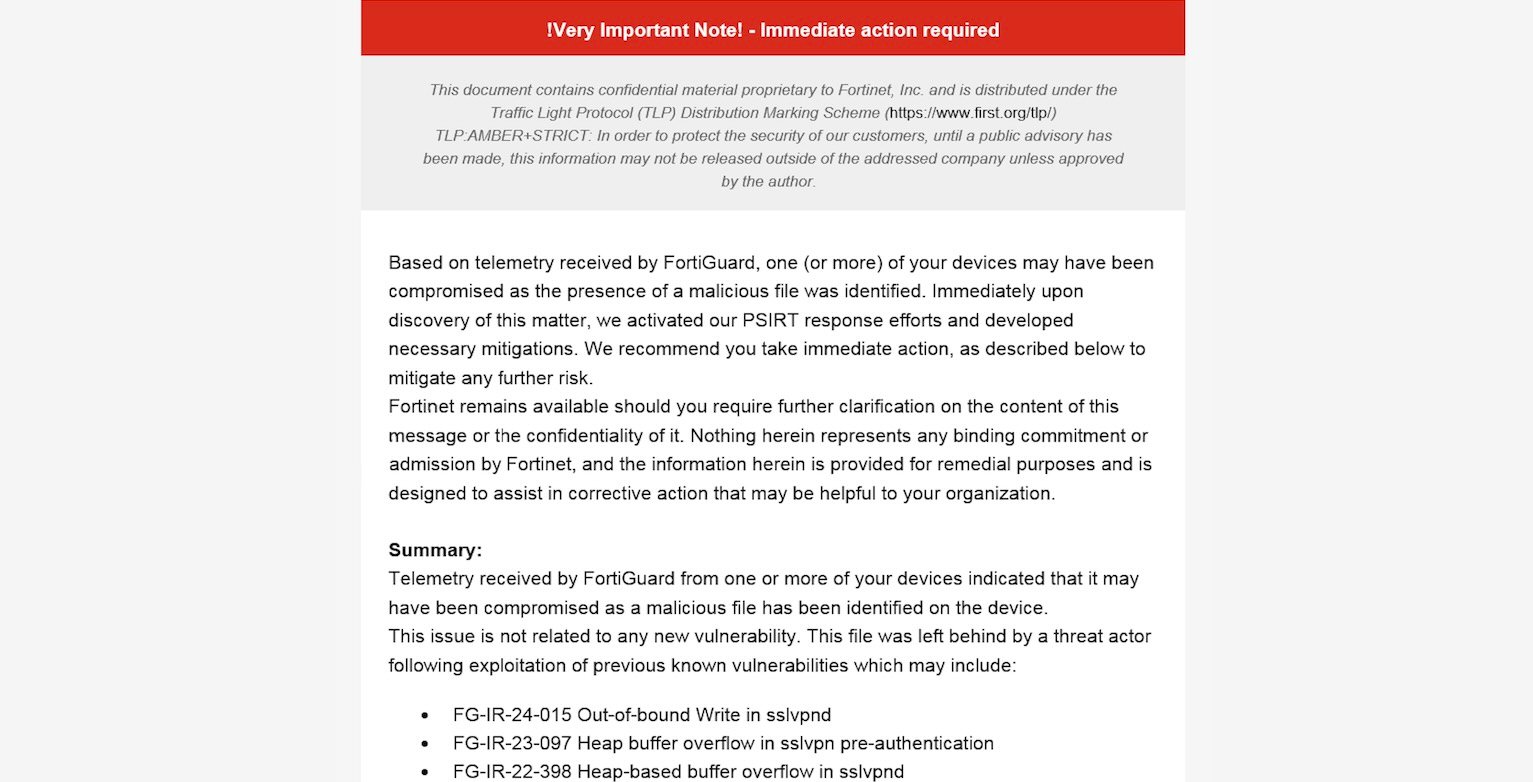
Fortinet has recently issued a critical warning regarding a sophisticated post-exploitation technique that enables threat actors to maintain unauthorized read-only access to FortiGate VPN devices, even after vulnerabilities have been patched.
How Hackers Maintain Access
Attackers have leveraged symbolic links in device language files folders, linking directly to the root filesystem. This breach tactic specifically targets devices with SSL-VPN enabled and allows hackers ongoing access via the publicly available SSL-VPN web panel.
Detailed Advisory by Fortinet
Upon discovering unusual activities, Fortinet emailed affected customers urging immediate action. Fortinet confirmed that this exploitation did not stem from a new vulnerability but rather from overlooked modifications during previous breaches involving CVE identifiers CVE-2022-42475, CVE-2023-27997, and CVE-2024-21762.
Global Impact and Response
The exploitation technique has reportedly been part of a massive series of attacks since early 2023, notably impacting numerous devices across France. Both the French Computer Emergency Response Team (CERT-FR) and the Cybersecurity and Infrastructure Security Agency (CISA) have acknowledged the severity of this situation and recommended network defenders report any anomalies.
Urgent Recommendations for Network Administrators
- Immediate Firmware Updates: Fortinet advises installing the latest firmware updates to eliminate any backdoors left by attackers.
- Rigorous Configuration Reviews: Administrators should promptly check for any unusual configuration changes.
- Isolate and Reset: Isolating affected VPN devices and resetting all sensitive information is crucial to prevent further damage.
Preventive Measures and Further Guidance
For detailed steps on safeguarding devices against such vulnerabilities, Fortinet has provided extensive guidance for resetting potentially exposed credentials and reinforcing security measures.
Stay Informed and Secure
Understanding the tactics employed by cybercriminals can significantly enhance an organization’s defense mechanisms. Regularly updating systems and staying vigilant about security advisories is paramount.
Conclusion
While Fortinet has been proactive in notifying customers and patching known vulnerabilities, the persistence of unauthorized access highlights the need for continual vigilance and immediate action in cybersecurity practices.
For more information, refer to the original advisory and ensure your network’s security parameters are up to date.
Related: Western Sydney University discloses security breaches, data leak
Last Updated: April 11, 2025




