Urgent Security Alert for Fortinet Device Users
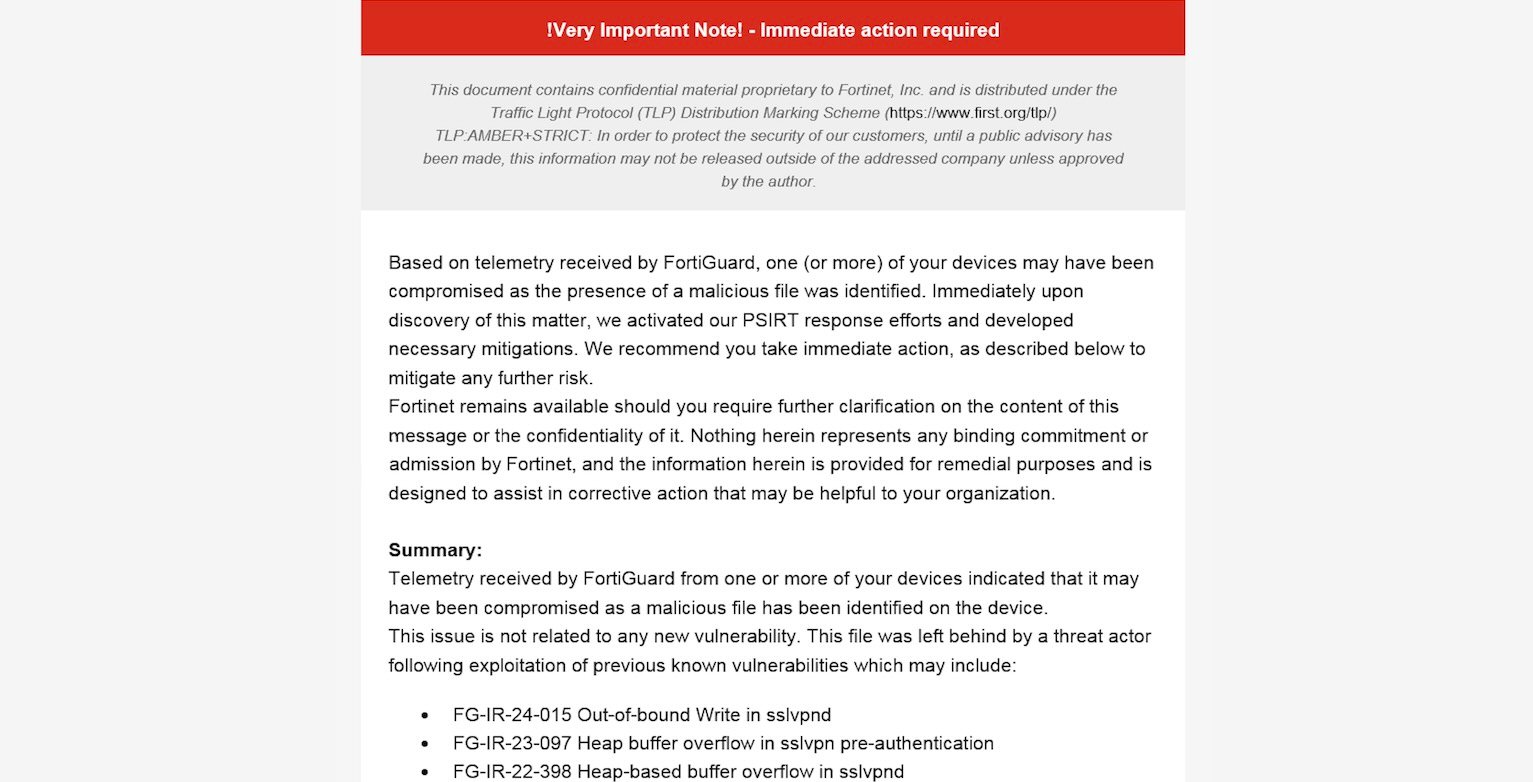
Security experts have uncovered a breach impacting over 16,000 Fortinet devices globally. A sophisticated symlink backdoor has been employed, granting unauthorized read-only access to sensitive files. This cybersecurity breach raises significant concerns about data security and device integrity.
Details of the Breach
The Shadowserver Foundation, a respected threat monitoring platform, has increased initial estimates from 14,000 to now confirming 16,620 devices affected. This discovery reflects an alarming escalation in the cybersecurity threat landscape, specifically targeting previously compromised devices that were believed to be secured.
How the Breach Occurred
Fortinet recently alerted its customers to a new persistence mechanism used by cybercriminals to maintain remote access to critical files. This was not due to fresh vulnerabilities but linked to prior zero-day exploits used to infiltrate FortiOS-powered devices throughout 2023 and projected into 2024.
The attackers ingeniously used symbolic links in the language files directory to gain continuous access to the root filesystem on SSL-VPN enabled devices. These language files, typically public, became the gateway for persistent exploitation even post-patch updates.
Fortinet’s Response to the Threat
In efforts to mitigate this breach, Fortinet has deployed an updated AV/IPS signature that effectively identifies and eliminates the malicious links. Additionally, firmware updates have enhanced protections to prevent similar attacks.
This month, Fortinet took proactive steps by emailing affected customers, advising them on the breach and necessary security measures.
Recommended Security Measures
Given the scale of this breach and potential access to sensitive configuration files and credentials, it is critical for administrators and users to take immediate action:
- Reset all credentials: Compromised devices might have exposed user credentials, necessitating a comprehensive reset.
- Audit and Update: Ensure that all devices are running the latest FortiOS versions and security patches.
- Follow best practices: Referencing Fortinet’s recommended security measures can provide further guidance for securing compromised devices.
Conclusion
The incident underscores the need for vigilance and swift action in the face of cybersecurity threats. Device users and administrators must stay informed and act decisively to protect their networks from further exposure.
For ongoing updates and more detailed analysis, refer to the dedicated reporting by the Shadowserver Foundation on their statistics dashboard.
Related: How the Jira Outage is Affecting Global Users: Key Insights into Recent Dashboard
Last Updated: April 16, 2025




